The Identity Crisis of Agentic AI: Lessons from the OpenClaw Saga


The Identity Crisis of Agentic AI: Lessons from the OpenClaw Saga
February 3, 2026
5
min read
Decoded: The Difference Between Consumer Copilot, Copilot Chat, and Microsoft 365 Copilot
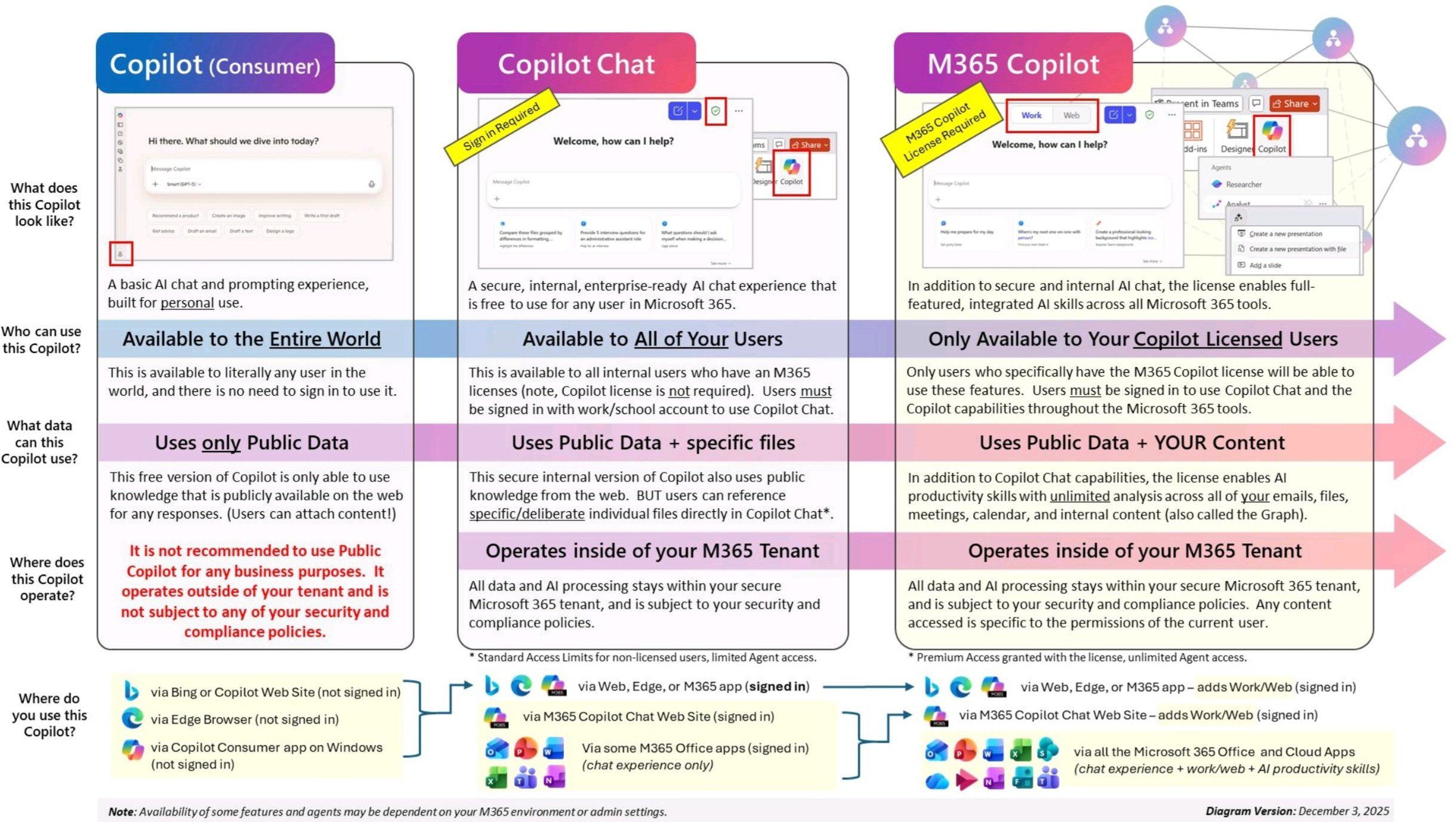

Decoded: The Difference Between Consumer Copilot, Copilot Chat, and Microsoft 365 Copilot
December 5, 2025
2
min read
The Fork in the Road: Artificial Intelligence, Labor Economics, and the Future of Civilization


The Fork in the Road: Artificial Intelligence, Labor Economics, and the Future of Civilization
December 2, 2025
14
min read
Work IQ, Fabric IQ, and Foundry IQ: The New Semantic Architecture of Agentic AI
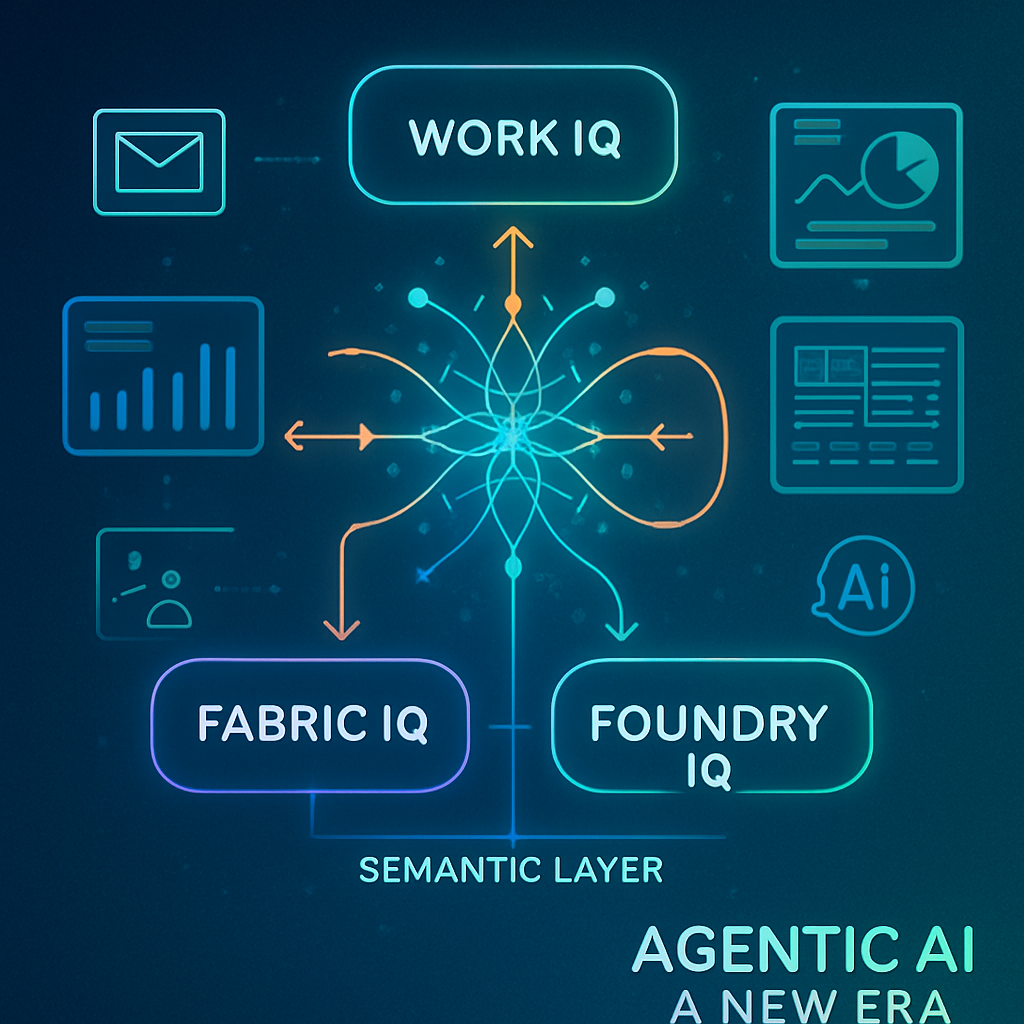

Work IQ, Fabric IQ, and Foundry IQ: The New Semantic Architecture of Agentic AI
November 19, 2025
4
min read
The Agentic Enterprise is Here: 10 Takeaways from Microsoft Ignite 2025


The Agentic Enterprise is Here: 10 Takeaways from Microsoft Ignite 2025
November 19, 2025
5
min read
From Potential to Production: A Strategic Guide to Building Enterprise-Ready Agents on Azure

From Potential to Production: A Strategic Guide to Building Enterprise-Ready Agents on Azure
November 6, 2025
3
min read
Beyond the Algorithm: The Three Pillars of True AI Enablement


Beyond the Algorithm: The Three Pillars of True AI Enablement
October 28, 2025
6
min read
The New Phishing Training: Building a Human Firewall for AI


The New Phishing Training: Building a Human Firewall for AI
October 27, 2025
3
min read
Red-Teaming AI: Hacking Your Own AI Before the Adversaries Do


Red-Teaming AI: Hacking Your Own AI Before the Adversaries Do
October 21, 2025
3
min read
Your AI Is Leaking Secrets: Model Inversion and the New Data Breach


Your AI Is Leaking Secrets: Model Inversion and the New Data Breach
October 21, 2025
3
min read
Data Poisoning: The Sleeper Threat That Corrupts AI from Within


Data Poisoning: The Sleeper Threat That Corrupts AI from Within
October 14, 2025
3
min read
Social Engineering for AIs: How Prompt Injection Hijacks Your LLM


Social Engineering for AIs: How Prompt Injection Hijacks Your LLM
October 8, 2025
3
min read


