The New Phishing Training: Building a Human Firewall for AI


The New Phishing Training: Building a Human Firewall for AI
October 27, 2025
3
min read
Red-Teaming AI: Hacking Your Own AI Before the Adversaries Do


Red-Teaming AI: Hacking Your Own AI Before the Adversaries Do
October 21, 2025
3
min read
Your AI Is Leaking Secrets: Model Inversion and the New Data Breach


Your AI Is Leaking Secrets: Model Inversion and the New Data Breach
October 21, 2025
3
min read
Data Poisoning: The Sleeper Threat That Corrupts AI from Within


Data Poisoning: The Sleeper Threat That Corrupts AI from Within
October 14, 2025
3
min read
Social Engineering for AIs: How Prompt Injection Hijacks Your LLM


Social Engineering for AIs: How Prompt Injection Hijacks Your LLM
October 8, 2025
3
min read
Your Company's New Brain is Under Attack: An Introduction to the AI Threat Surface

Your Company's New Brain is Under Attack: An Introduction to the AI Threat Surface
October 6, 2025
3
min read
Cybersecurity Awareness Month 2025: Your Guide to the AI Security Frontier


Cybersecurity Awareness Month 2025: Your Guide to the AI Security Frontier
October 3, 2025
3
min read
Why Microsoft Purview DSPM is a Game-Changer for Regulated Industries


Why Microsoft Purview DSPM is a Game-Changer for Regulated Industries
June 23, 2025
4
min read
The High Cost of Ignoring Cybersecurity Requirements: A Tale of Non-Compliance and Consequence


The High Cost of Ignoring Cybersecurity Requirements: A Tale of Non-Compliance and Consequence
August 24, 2024
2
min read
Writing an Effective Security Incident Response Procedure

Writing an Effective Security Incident Response Procedure
November 25, 2019
4
min read
PSA: Patch BlueKeep and DejaBlue Now


PSA: Patch BlueKeep and DejaBlue Now
October 28, 2019
2
min read
The Fundamentals of a Strong Cybersecurity Framework
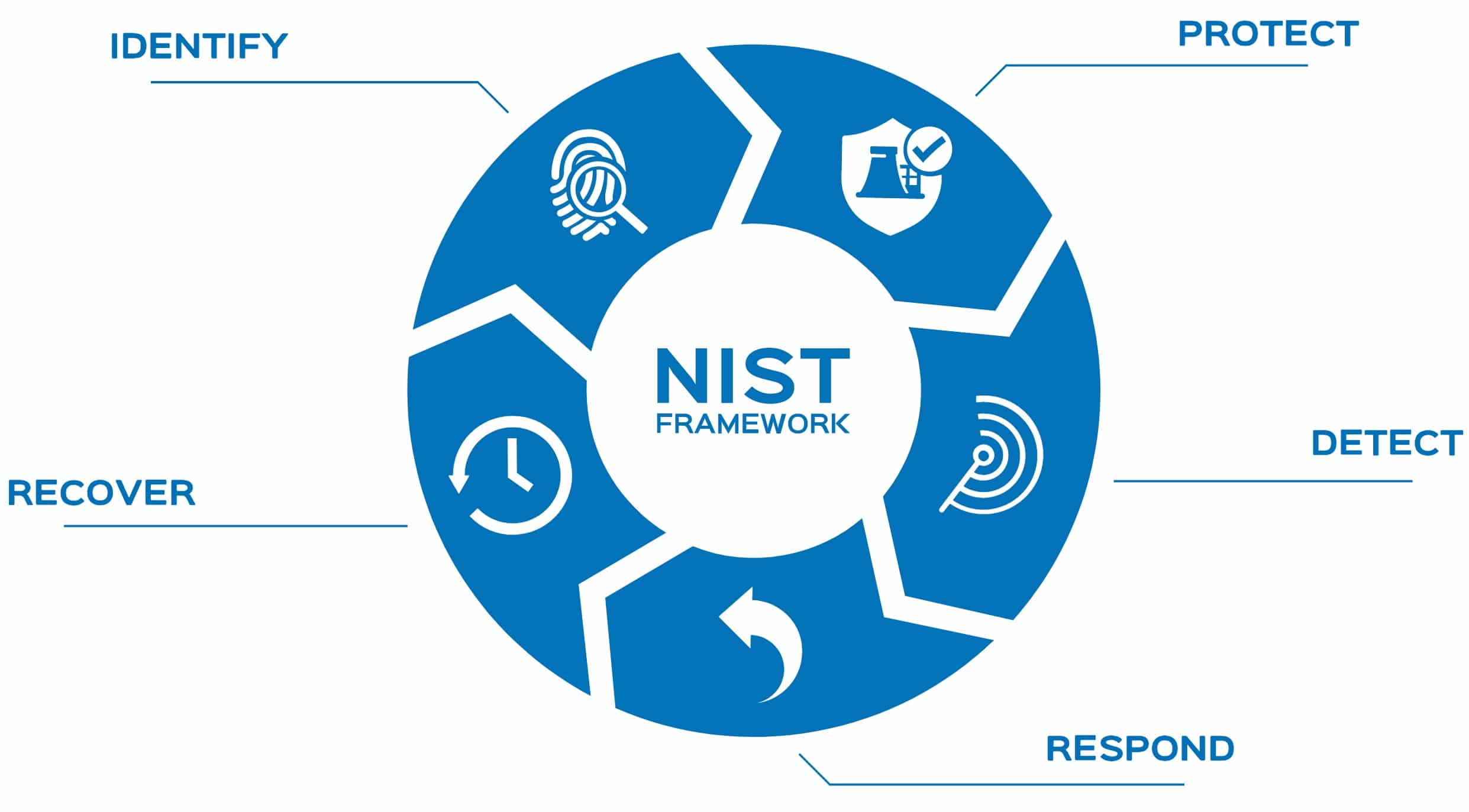

The Fundamentals of a Strong Cybersecurity Framework
July 15, 2019
4
min read


