The Fundamentals of a Strong Cybersecurity Framework
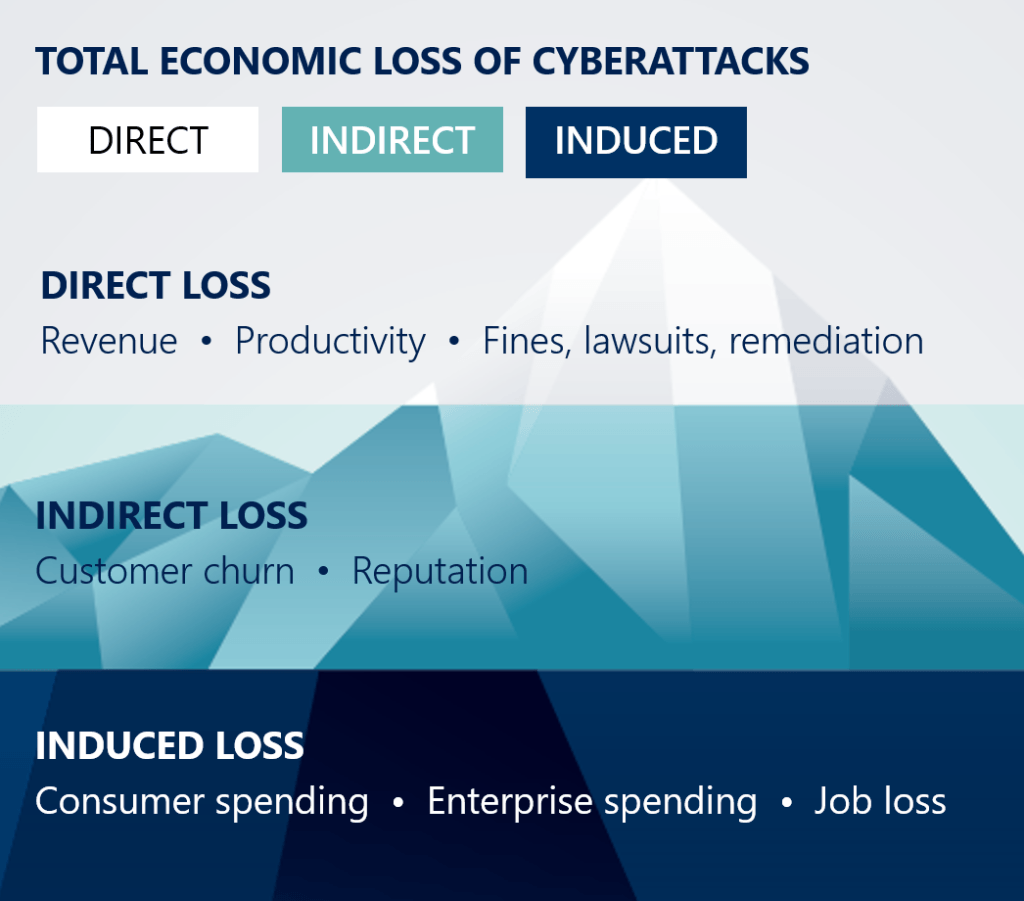
The intent of implementing a cybersecurity framework is to increase the effort of an attacker to gain privileged access. By breaking the attacker's economic attack model, you can effectively secure an attack vector. If we look at the statistics regarding data breaches, the sheer number of incidents has grown exponentially over the last 10 years or so. There are three main reasons for this:
- More malicious actors realizing the value of stolen/illegally accessed data.
- Increased system complexity, leading to the possibility of human error.
- A surge in data across the board, providing more opportunities for security issues.
Why Do You Need A Security Framework?
At the core, what a cybersecurity framework does versus simply “winging it,” is allowing your cybersecurity team to reap the benefits of the successes and failures of other teams. What does this mean? In essence, when a team puts together a piecemeal cybersecurity strategy, the only frames of reference they have are their personal knowledge, and maybe what they can dredge up from a Google search. A security framework, especially adopting an existing framework, means that you can incorporate proven knowledge and strategy, and apply it to your security plans.
In addition, when you use an existing security framework, you have access not only to the information it was based on, but also a growing culture and community around it. Have a question about a piece of software? Some of your contemporaries are likely able to help. You don’t get this informal level of support with a haphazard security plan.
Utilizing the NIST Cybersecurity Framework
There are a variety of different security framework options out there. One of our preferred frameworks at Infused Innovation is the NIST Cyber Security Framework. This is because it can be mostly achieved by standardizing on Microsoft tools. It has the additional benefit applying to controls from a number of other frameworks.
These basic principles run off of five main points. We’ll cover what exactly they entail, and what Microsoft products/software get used with each application.
Identify
The basic principle here is to help your organization gain the understanding it needs to understand potential risks to your data and systems as they arise. One way to do this in practice is by using Microsoft’s Azure Active Directory for asset and user identity management. This addresses one of the major sources of data breaches, which is outside actors gaining access to one user’s information.
Along with this goes understanding existing regulations to provide top compliance. You can see this with the Compliance Manager in the Microsoft Trust Portal.
Protect
This mainly covers the development and implementation of safeguards, after you’ve identified risk areas, to ensure that your data is kept secure. Identity management (which we alluded to before) is a major part of it, but some of this has nothing to do with tech at all. For example, human error is still a major part of data breaches across the world. Investing in proper training and best practices fall into this category.
Even with end-user phishing training, we typically still see around a 5% click through rate on phishing attacks. To help mitigate this risk even further, we recommend adding Office 365 Advanced Threat Protection (ATP) to your licensing to scan email URLs for malicious threats at the time the user clicks the link. Microsoft 365 Business is a great SKU for small business that includes Office ATP and it is our suggested starting point for most organizations.
Detect
This has a similar, but separate function to the identify category. While Identify is more about finding potential risk areas in your security, detect is more about having active measures to detect a cybersecurity event when it does occur. For example, Microsoft 365 E5 includes Azure ATP and Microsoft Defender ATP, with the capacity to detect thousands of suspicious activities that can occur throughout a cyber attack. Not only will it alert your team, but also other security systems to protect other aspects of your enterprise.
Can your current anti-virus block you from signing into Office 365 if it detects a threat? If you're using Defender ATP with risk-based conditional access, it will. When we deploy the Microsoft 365 E5 suite, we configure fully automated investigation and response workflows across your tenant.
Respond
Naturally, after you find a cybersecurity issue, you need to have a way to act. Proper training on how to react to cyber attacks is essential for your team, but the NIST framework includes some tech help here, also. For example, Microsoft Defender ATP (formerly Windows Defender ATP) allows you to take response actions on machines and files to mitigate damage malicious actors may cause.
Closing Thoughts on Having a Strong Cybersecurity Framework
This is only a basic roadmap of one of the ideal ways that you can put together a proper cybersecurity framework. Not only do you get increased protection for your sensitive data and other information, but when you do need to make changes and other adaptations, these will be easier to change as needed. This is a lot more than just throwing the latest tech at a situation, though.
What do we mean by this? It’s important for businesses planning on putting together a cybersecurity framework to try and take a holistic view of the situation. They need to make sure that they take the time to figure out their exact needs, and a solution that can properly match them. At Infused Innovations, we can help you find and implement said solution. Our goal is to help all companies integrate the changes and advancements they need to compete as technology iterates and advances.
If you do not have any regulatory requirements, we typically suggest at least one, but typically a combination of the following options:
- Follow as many Microsoft Secure Score recommendations as you leadership will approve
- Implementing as much of the NIST CSF Framework without annoying users
- Implementing as much of ISO27001 without annoying users
- Review and consider implementing CIS or Azure CIS recommendations
When you are ready to take a new view of cybersecurity frameworks, we are ready to help. Reach out to us for a consultation today.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Pricing for MDE P1 - Microsoft Defender for Endpoint is Getting a New SKU

Microsoft Defender for Endpoint and Intel TDT Combine for a New Ransomware Defense

No Comments Yet
Let us know what you think