Shadow IT Discovery with Microsoft Cloud App Security
Apps! You run the world! I can just hear Beyonce's voice in my head--mainly because I just listened to it on Google Play Music. And by continuously monitoring Shadow IT Discovery with Microsoft Cloud App Security (MCAS), which is built-in natively on Windows 10 devices, Azure also knows that I just listened to Google Play Music. Even though I work remotely.
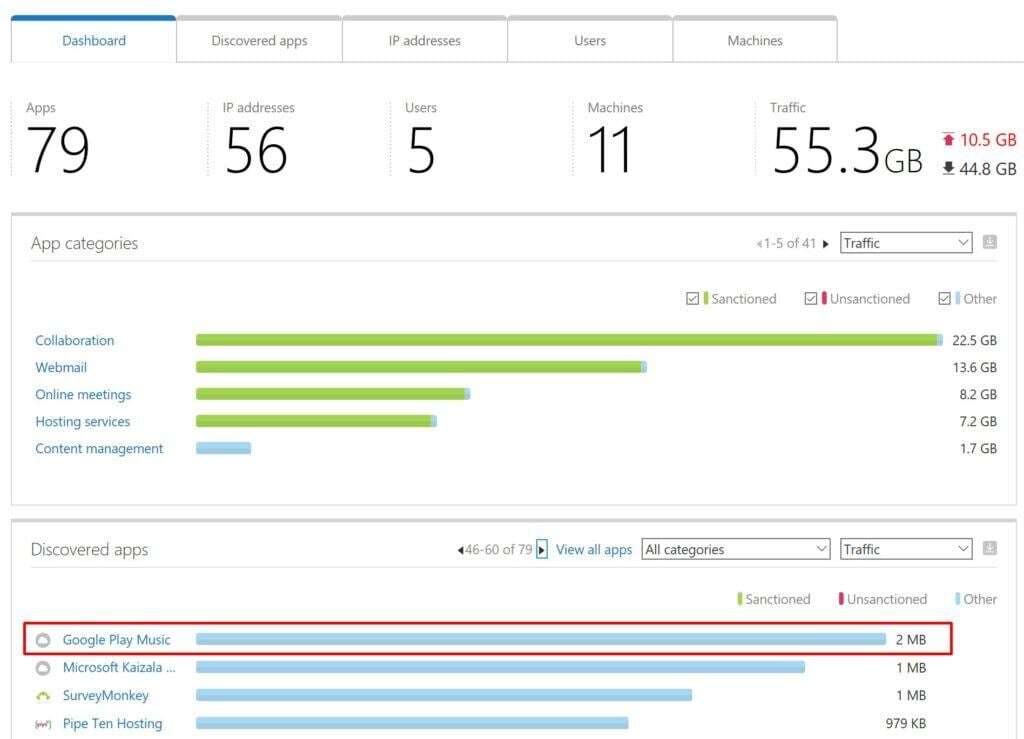
Far beyond my own personal use, though, Microsoft's data shows that employees in large organizations access over 1,000 different apps. Some of these are on-premises, some are cloud-based, and some are custom line-of-business. But of all these apps employees are using, less than 10% are IT-managed. So it's time to step up app security in the workplace, and Microsoft Cloud App Security is here to help with that.
Using App Connectors for Discovered Applications
App connectors allow you to onboard the following cloud SaaS platforms and monitor your organization's data that is being shared with each platform:
Using App Connectors, it allows you to enable Conditional Access App Controls. App Controls use a reverse proxy architecture that integrates natively with Azure AD's Conditional Access feature. After onboarding third-party apps, you can then create rich access management rules that behave as though the data is stored natively in Microsoft's cloud even though it's already left your Office 365 tenant.
Microsoft Cloud App Security extends Conditional Access support
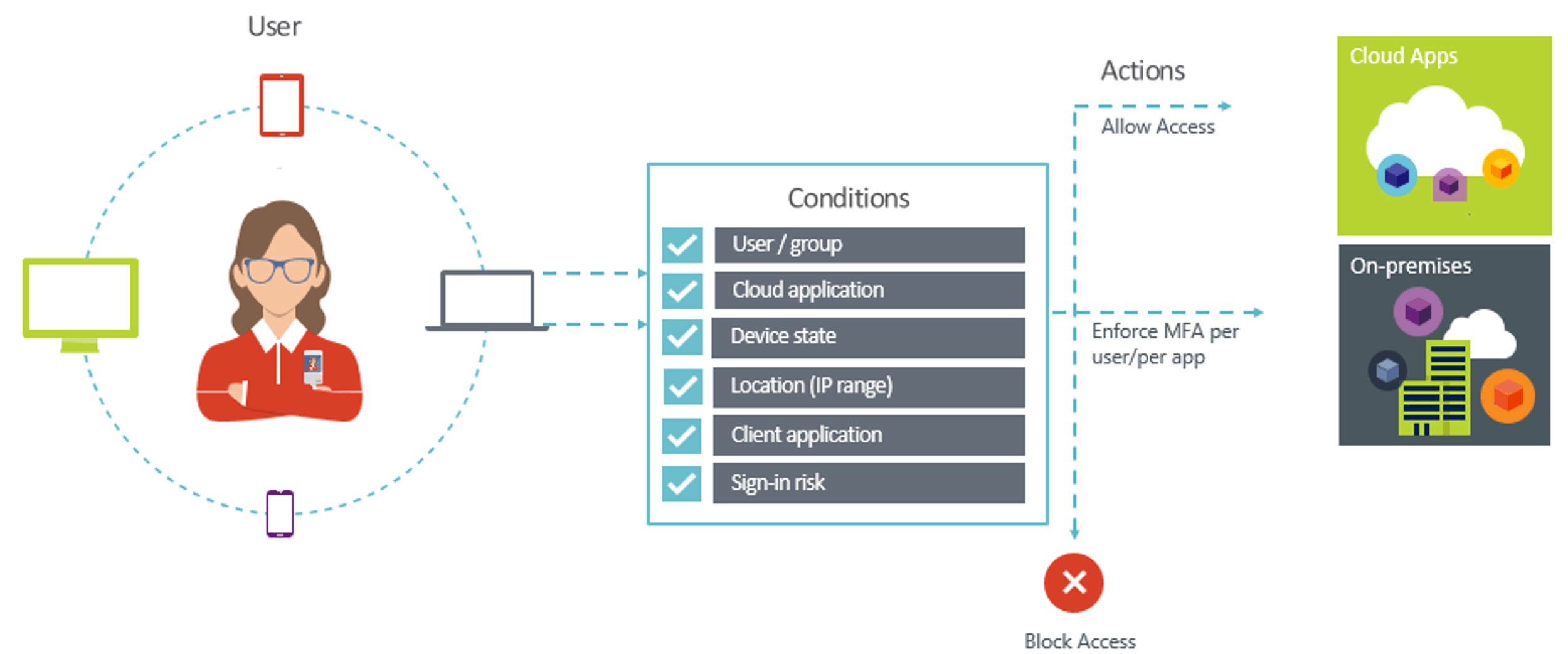
This builds off of Microsoft's already helpful Conditional Access App Control, which offers support for featured applications. As its name implies, it sets up conditions that determine where and to whom the policy should apply. Some of the capabilities of Conditional Access when integrated with MCAS are:
- Blocking uploads or downloads of sensitive data on personal devices
- Preventing data exfiltration
- Monitoring user behavior and enforcing data compliance policies
- Barring risky activities within certain apps, or specific uses of particular apps
A handy centralized activity log allows administrators to use filters to view certain activities or specific files. This makes it easier to track patterns and set automatic processes to avoid unsafe scenarios. Here's an example of how Conditional Access can block an action based on the condition of an unmanaged device:
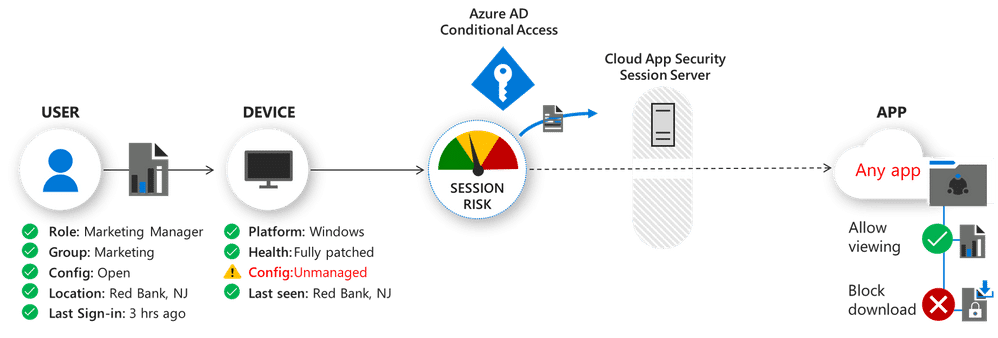
Now Microsoft Cloud App Security can protect any app in the work environment, regardless of its type. It offers centralized and standardized real-time control for all of the apps employees use in an organization. (To be sure to make your apps compatible, cloud apps should leverage SAML 2.0 or Open ID Connect and make use of single sign-on in Azure AD. Configure on-premises apps with Azure AD App Proxy and Kerberos Constrained Delegation. If you're already familiar with Conditional Access, it will likely follow that your previously unmanaged applications will make the cut.)
Shadow IT Discovery with Microsoft Cloud App Security is Easy to Deploy
Enabling MCAS on Windows 10 devices is a breeze, but it does require additional licensing. You'll need Microsoft Defender ATP licenses to ship the logs from your Windows 10 devices, and then you'll need MCAS licenses to interpret the data. Both of these SKUs are available in the Microsoft 365 E5 and M365 E5 Security bundles.
After you purchase your licenses, it's three steps to adopt newly discovered apps:
- Connect the app in the Microsoft Cloud App Security portal.
- Validate telemetry between Azure AD and your third-party app.
- Enable policies with a simple GUI-driven checkbox deployment to configure conditional access policies.
A small PoC deployment can be completed in as little as an hour. Then you can go home and enjoy your favorite personal app. Or play outside with your kids instead. Either way, you'll have the peace of mind that comes with smart security for all of your workplace's apps.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Better together: Conditional Access with Azure MFA (Multifactor Authentication)

Microsoft's Windows Defender AV Earns "Top Product" Award in June 2019 Antivirus Comparison

No Comments Yet
Let us know what you think