Cybersecurity Automation with Azure Sentinel for SIEM and SOAR
Traditional security operations centers could get away with pre-set prevention technology and detection mechanisms based on prior knowledge of attack methods. But in the past few years threats have developed rapidly in both number and sophistication. It's no longer enough to look at intelligence as a one-way product addressing occasional threats. Moreover, not all threats can be predicted and prevented ahead of time. Today security leaders must operate on the assumption that their SOCs are continually under evolving threats and be ready to respond with adaptive intelligence. They need to be thinking cybersecurity automation.
SIEM: Powerful but Limited Security
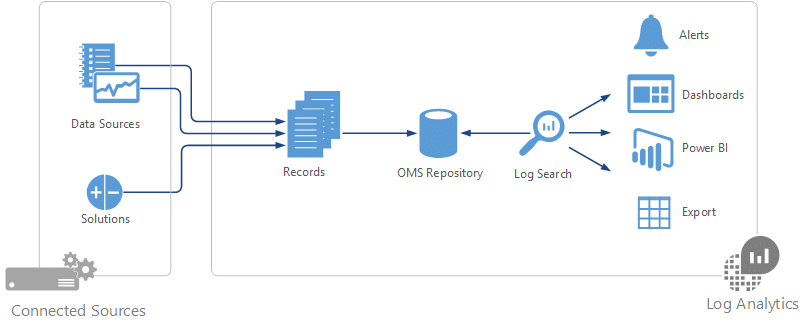
Security Information and Event Management (SIEM) combines the advantages of long-term information storage and analysis (SIM) with real-time monitoring of events (SEM). This can take the form of software or service. The SIEM's job is to aggregate and analyze data, identify threats and alert the security team when they appear. It uses a variety of security tools to centralize comprehensive data that can be crucial in keeping track of potential hazards.
There are two big limitations to SIEM, though. For one, it operates from a standard baseline that needs to be updated manually as the environment evolves. Ankit Bose at PricewaterhouseCoopers even likens a SIEM to a baby because it needs to be "fed" and fine-tuned regularly. Furthermore, its large amounts of data and ensuing alerts add up to a big workload. The SIEM identifies threats, but it doesn't itself act against them.
SOAR: SIEM's Turbo-Boosted Sidekick
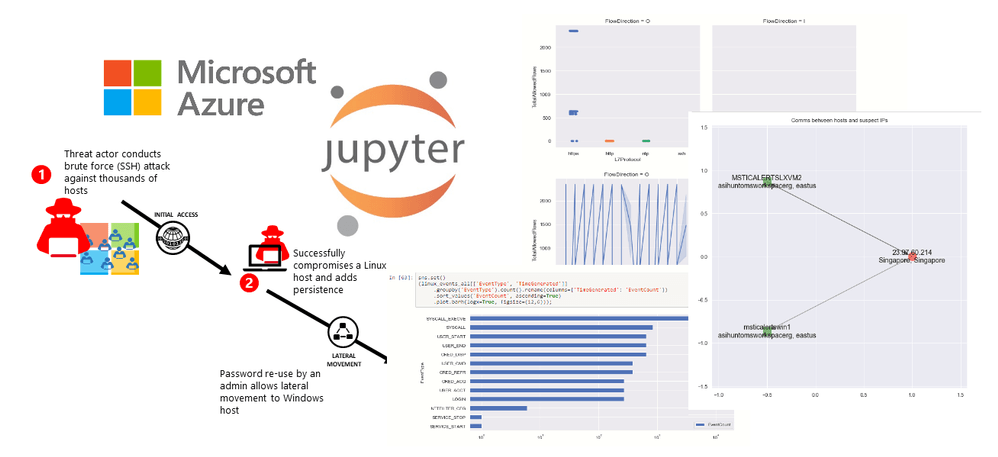
SIEMs are so good at finding threats, they end up generating more alerts than security teams can handle manually. That's where Security Orchestration, Automation and Response (SOAR) comes in. SOAR platforms can take action in response to particular kinds of incidents using something called playbooks. This allows for immediate decision-making and automatic responses to certain alerts. It also frees up time for security teams to address only the threats that genuinely need a human analyst. SOAR provides context-adaptive, intelligence-driven solutions with the capacity to take on evolving threats.
Azure Sentinel provides rich SOAR capabilities through Fusion and Jupyter notebooks integration. At Infused Innovations, our Secqur Aether service provides co-managed SIEM and SOAR services to keep your automation up-to-date.
The Increasing Necessity for Cybersecurity Automation
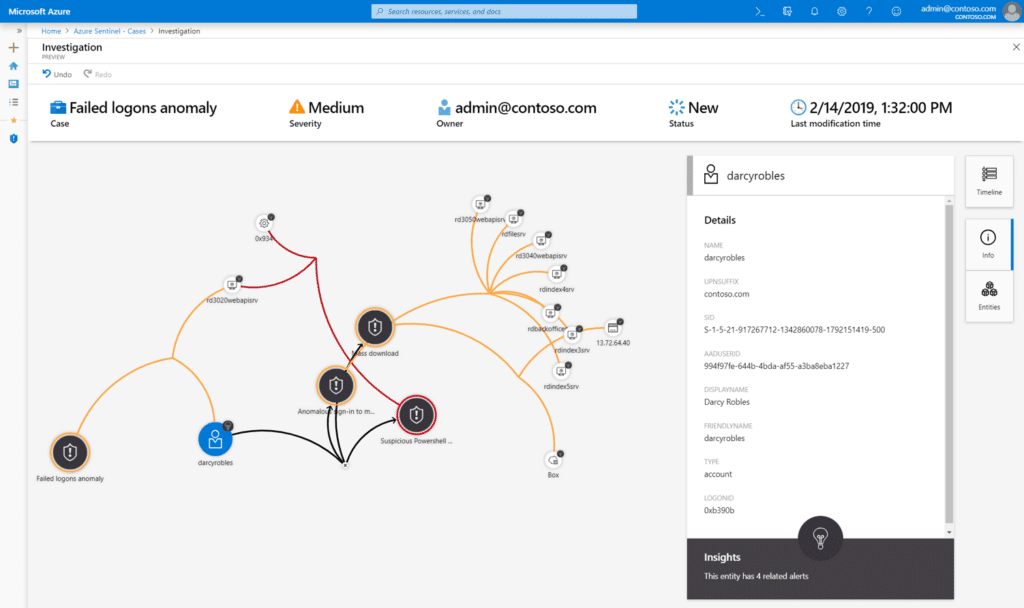
This is important because today's cyber threats are growing rapidly in both number and sophistication. Because of this constant evolution, security teams are bombarded with alerts. Much of the work responding to these alerts is repetitive and time-consuming. Automating responses through technology like SOAR is becoming not only helpful but necessary to prevent a compromised Security Operations Center. Forrester predicts a shortage of 2 million security workers by 2022, and Cybersecurity Ventures puts the number at 3.5 million by 2021. Successful SOCs in the modern environment will have no choice but to take a proactive, adaptive approach that automates processes wherever possible.
Azure Sentinel: SIEM and SOAR together!
Lucky for these SOCs, there is a scalable, cloud-native solution that combines the strengths of both SIEM and SOAR. It's called Azure Sentinel, and it's the best marriage since peanut butter and jelly. Its preview is now available to showcase its abilities not only to collect data, detect threats, and investigate with AI, but also to respond rapidly and automatically.

Sound intriguing? Optimize your company's cybersecurity automation by checking out our guide on how to deploy Azure Sentinel.
Closing Thoughts on Cybersecurity Automation with Azure Sentinel
Cybersecurity has typically been a thankless task with high burn out rates. SOCs need to have a robust training plan due to the high turnover rates of security analysts and limited availability of resources on the open job market. Luckily, automation with SIEM and SOAR can ease the burdens of internal cybersecurity controls, monitoring, and threat hunting. By leveraging Microsoft's cloud security stack, we can gain full visibility into a breach within 1-2 hours. Most threats that we deal with in Office 365 are isolated and eliminated within 12 hours of discovering the breach. Compare this to the weeks of downtime that the cities of Atlanta and Baltimore suffered by not having enough cybersecurity controls in place.
Let your IT department focus on empowering your users and growing your business. Consider reaching out to a Microsoft Gold Partner to help monitor, update, and secure your Microsoft cloud.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Pricing for Azure Sentinel is GA
Guide to Deploy Gen2 VMs in Azure

No Comments Yet
Let us know what you think