Better together: Conditional Access with Azure MFA (Multifactor Authentication)
As enabling multifactor authentication is the number one security recommendation to improve your Microsoft Secure Score, let’s take a look at why it's better to deploy Conditional Access with Azure MFA together. We'll walk through deploying Azure MFA for all of your users in a single day and most users won’t even notice!
Isn’t Office 365 already secure? Why do I need to enable Conditional Access with Azure MFA?
When your Exchange server was running on-premises, you probably required your users to VPN into the network using certificate authentication before they could access their email. While not a one-time token, this was a form of MFA: you needed a company-issued certificate, a successful connection to a VPN, and your account credentials.
Now that Exchange is running in the cloud, it’s important to keep in mind the shared responsibility for cloud computing to keep your data secure. Sure, Microsoft has armed guards protecting their datacenters, but it’s still up to you to limit the ways your users can access data.
As noted in a previous blog, here is an example of login attempts from around the world for a US based company with less than 10 employees:
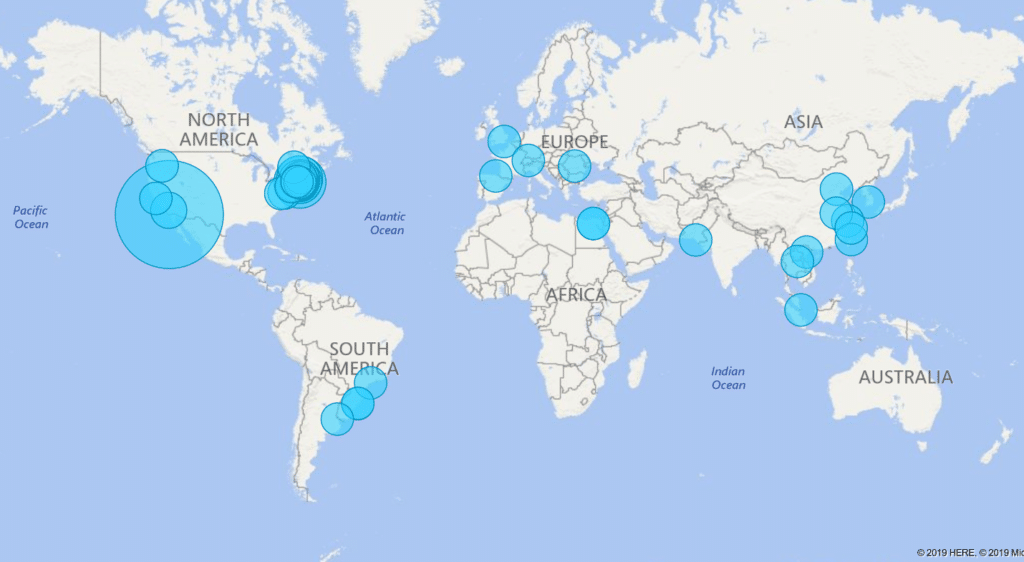
Microsoft filters out most of this noise as botnet attacks. However, if we know these are malicious attacks, let’s just move forward with targeting some conditional access policies to block them.
Overview
To deploy MFA with Azure AD, Infused Innovations recommends following these steps:
- Populate Azure Active Directory (AAD) with all your users
- For this blog, I’m assuming this step is already completed using Azure Active Directory Connect
- License your users with a SKU that includes at least Azure AD Premium 1 services
- Infused Innovations Recommends Microsoft 365 Business for organizations under 300 users or Microsoft 365 E3 with Identity Threat Protection for larger companies
- Configure Azure Multifactor Authentication (MFA) response challenges
- Configure Named Locations
- Create an Azure AD group for exempt users
- Create Risk-Based Conditional Access with Azure MFA policies
- Define a Conditional Access with Azure MFA break glass policy
- Configure Company Branding
- Create a custom banned password list
- For AAD P2 licensed users, configure Azure AD Identity Protection
- Create an email campaign for your users to enroll with Azure MFA
- Create additional conditional access policies to secure your environment
Configure Azure MFA Response Challenges
End users can configure Azure MFA and Self Service Password Reset at the same time in a single management portal. Prior to enforcing user registration, Infused Innovations recommends setting the following configurations for Authentication Methods:
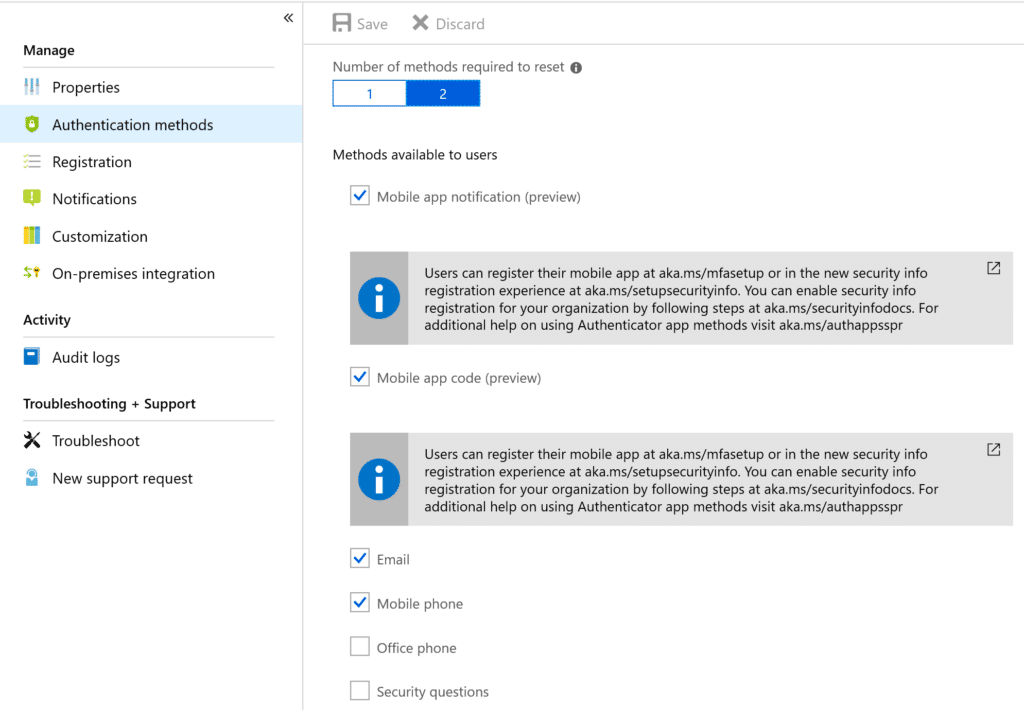
- Require 2 response challenges to reset a password
- Allow the following challenge types:
- Mobile App Notification
- Mobile App Code
- Mobile Phone
Infused Innovations discourages the mobile phone option as text previews are often displayed on the lock screen of a phone. As a result of social media making it easier to discover security question answers, we don't recommend this option either.
Configure Named Locations for Conditional Access with Azure MFA
Named locations help the Azure MFA service target conditional access policies, as well as reduce false positives for risky sign-in behavior. Infused Innovations recommends creating at least the following three locations:
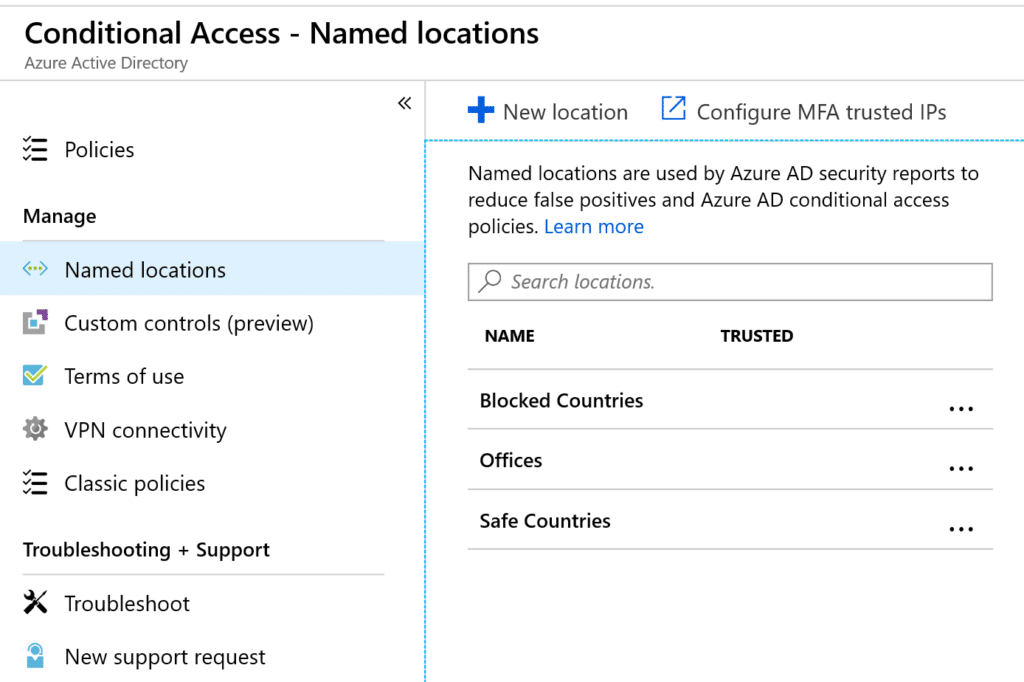
- Offices (The public IP addresses of your offices. Mark these as trusted locations.)
- Safe Countries (Typically the United States and any other countries that your staff travels to frequently)
- Blocked Countries (Typically Russia, China, North Korea, Iran, Nigeria, and unknown locations)
Create an Azure AD Group for Exempt Users
Inevitably, you will have a service account or a contractor from Moscow that will need to be exempted from some of these rules. If you would like to deploy Azure MFA in user batches, then you would probably start with the following security groups:
- All Users
- Exceptions - Travel Users
- Exceptions - Service Accounts
The Travel Users group could be used to allow users in foreign countries to login only from corporate-owned and compliant devices without having to respond to an MFA token challenge.
Create Risk-Based Conditional Access with Azure MFA Policies
For details on how to draft a conditional access policy, you can review the following Microsoft literature:
- 10,000 foot overview of CA: Conditional Access in Azure Active Directory.
- Conditional Access capabilities:Access controls in Azure Active Directory Conditional Access.
- Real-world use cases: Conditions in Azure Active Directory Conditional Access.
In a nutshell, conditional access is simply:

For our first rule, let’s create a rule named Block High Risk Countries to block those high risk countries:
| Condition | Value |
| Users and Groups | All Users; Except for Conditional Access Exceptions |
| Cloud Apps | All Cloud applications |
| Risk Levels | Recommendation: Target all risk profiles |
| Platforms | Recommendation: Target all platforms |
| Location | Blocked Countries |
| App Type | Recommendation: Target all app types |
| Device State | Recommendation: Target all device states |
| Grant | Block (or Require ALL MFA challenge types to be completed) |
Now let’s create a second rule named MFA in Foreign Countries to require an MFA challenge if a login is outside of your usual geography:
| Condition | Value |
| Users and Groups | All Users; Except for Conditional Access Exceptions |
| Cloud Apps | All Cloud applications |
| Risk Levels | Recommendation: Target all risk profiles |
| Platforms | Recommendation: Target all platforms |
| Location | Exclude: Safe Countries and Offices |
| App Type | Recommendation: Target all app types |
| Device State | Recommendation: Target all device states |
| Grant | Require one: MFA, Compliant Device, Hybrid AAD Joined Device |
You can optionally exclude the Travel Users group from this rule, and create a duplicate rule, but set the grant value to Require All instead of Require One.
And it’s that simple! You’ve just enabled Conditional Access with Azure MFA for all your users, and most of them should not have even noticed.
Create a Conditional Access with Azure MFA Break Glass Policy
In the fall of 2018, you may have heard that the Azure MFA service went offline for several hours and users were unable to login. In the event that this ever happens again, you should consider having a break glass policy—a global admin account that does not use Azure MFA so that it can disable Azure MFA during the outage.
One possible solution is to have a single account that uses Duo or AuthAnvil for an MFA challenge.
Another solution is to have a disabled Active Directory account that is a global admin but exempt from conditional access. To disable MFA, you would enable the account in AD, and force a sync with Azure AD Connect to enable the account for login to your tenant. Creating a monitoring alert that notifies all administrators if this account becomes active is highly recommended. Be sure to restrict interactive logins to a single privileged access workstation as well as a single public IP address.
Our final recommendation requires you to purchase your Office licensing from Infused Innovations. By signing of for Microsoft 365 CSP, we can work with you to use our secured tenant access to disable Conditional Access with Azure MFA in your environment during the outage.
Configure Azure AD Company Branding
This may seem like a very non-technical task, but configuring company branding in your portal can help prevent your users from falling for a phishing attack. The attacker would have to use your custom configuration instead of the generic Microsoft login page to perform the attack.
Follow this Microsoft guide to configure your portal.
Create a custom banned password list in Azure AD
Azure AD allows you to ban 1,000 custom passwords for cloud users for free. Infused Innovations recommends starting with this list of common passwords available on GitHub then add your organization’s name, and any common terms used in your industry to the list.
For Azure AD P2 licensed users, configure Azure AD Identity Protection
A future blog post will cover this topic more in-depth. For now, navigate over to the Azure Marketplace and enable Azure AD Identity Protection:
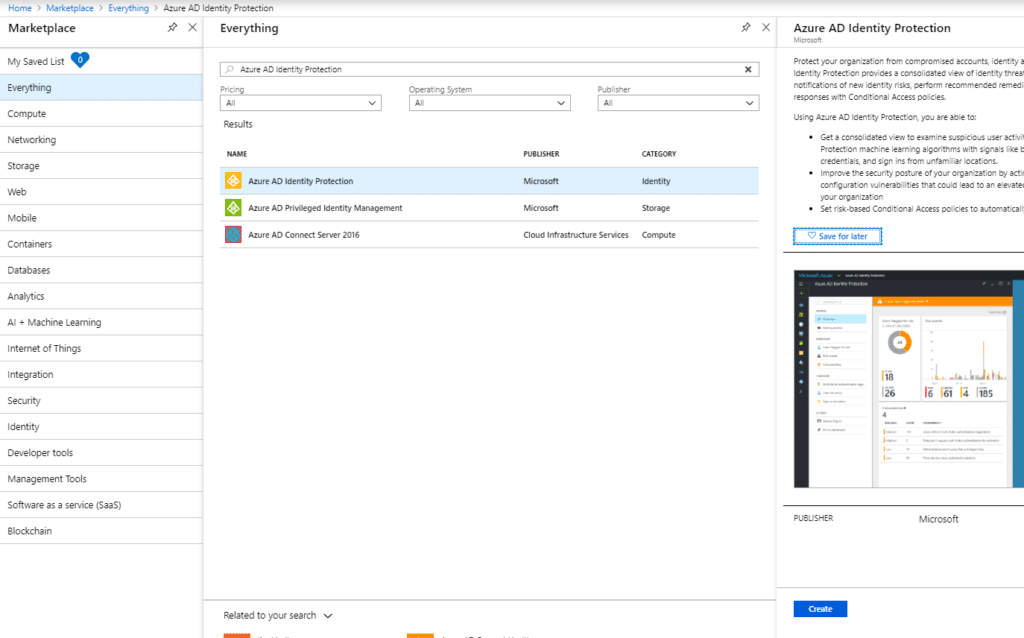
Turning this feature on will enable risk reporting for your tenant. Infused Innovations recommends configuring the User Risk Policy to force a password reset for any high-risk users.
The high-risk classification means that Microsoft is confident that the account has been breached. For instance, if Microsoft finds the user’s credentials on the dark web.
Create an email campaign for your users to enroll Conditional Access with Azure MFA
Now that you’ve enabled Conditional Access with Azure MFA for all your users in a handful of risky scenarios, the next step is enrolling your users. Consider customizing the Microsoft Fast Track rollout materials that are available here: https://www.microsoft.com/en-us/download/details.aspx?id=56768
Once your users are finished enrolling with Azure MFA, we suggest making more aggressive conditional access policies. For instance, always requiring Azure MFA for OWA logins or requiring Azure MFA on non-corporate owned devices.
One final thought: avoid using App Passwords. If you have an application that doesn’t support two-factor authentication, try to upgrade or replace that application.
Be sure to check out our other top suggestions to secure your Microsoft 365 environment. We also have an article on troubleshooting code challenges and SQL with Azure app insights.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Top 10 Security Best Practices with Microsoft 365 in 2021

Forrester Study Shows 123% ROI from Microsoft Azure AD
No Comments Yet
Let us know what you think