5 Ways to Reduce Your SOC's Alert Fatigue
With increasing digital and cloud-based work, cybersecurity threats are a continuous and growing concern. Large companies often have dozens of security products from multiple vendors in order to stay on top of these threats. Because of this reality, security operation centers (SOCs) face a deluge of alerts coming from every direction---so many, in fact, that a good portion of them never even get addressed. This is the "alert fatigue" that weakens an organization's security, and it isn't good cybersecurity management. How can companies do better? One way is to consolidate security vendors. As we've argued before, building a Zero Trust Security framework with 20+ vendors has zero chance of success. And we believe that the strongest overall provider for cybersecurity is Microsoft. Here are five ways working with Microsoft can reduce your SOC's alert fatigue.
Threat Intelligence
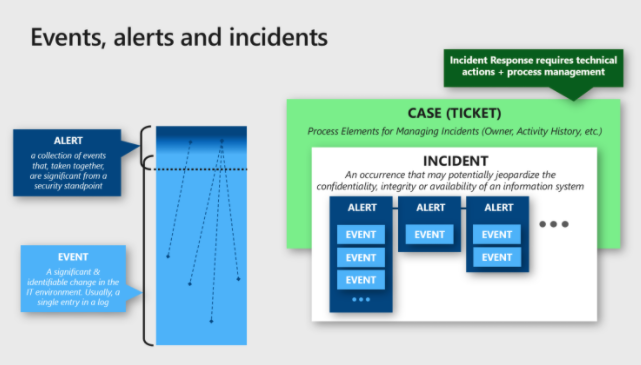
SOCs deal with continuous alerts about events and incidents, generating case tickets that are sometimes urgent and sometimes innocuous. Microsoft's threat protection helps sift through that and relieve much of the burden of finding what truly needs to be addressed. Taking a broad view of an organization's entire cybersecurity ecosystem, it looks at all the platforms and cloud environments it may be using. It covers all this massive information by using automation, artificial intelligence, and machine learning. These automated technologies allow for intelligent protection from threats without bombarding SOCs with alerts that they can't keep up with or don't need to see.
Integration
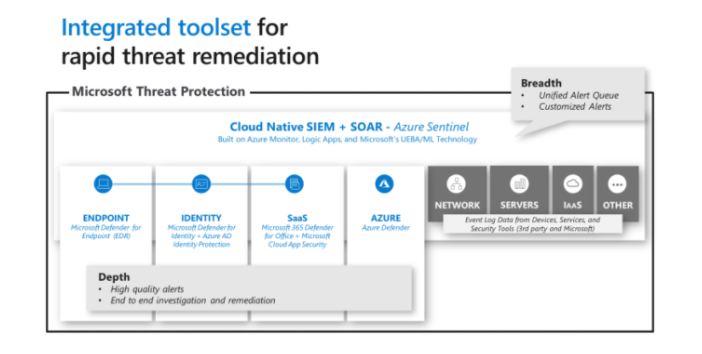
Signals and alerts are most efficiently managed when they are well integrated. Multiple and disparate sources can be a headache to keep track of, so the native integration between elements of Microsoft's protection stack is a welcome simplification. Incidents can be grouped and analyzed together to give a better sense of the company's vulnerabilities. Third-party data can also be integrated into this process so it's presented within the same uniform view.
User & Entity Behavior Analytics
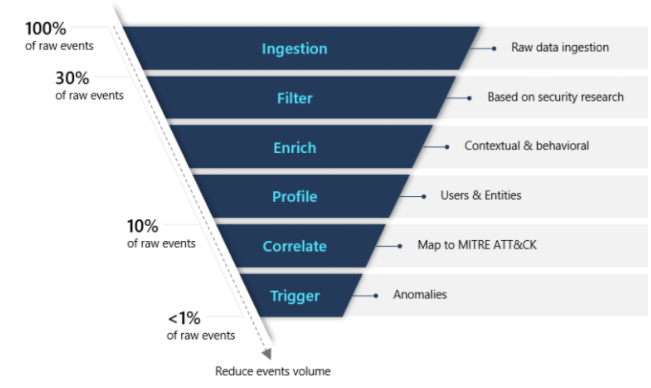
It's helpful to track User & Entity Behavior Analytics (UEBA) to get a sense of things like compromised entities, misused privilege, and insider risk. Microsoft's Azure Sentinel has UEBA natively built in. It monitors and analyzes entities like IP addresses, applications, users, and hosts, and it creates baseline behavioral patterns of these entities. When compared to this context, potential threats are better assessed. This way false alerts can be filtered out and only the most relevant information is left for the SOC team.
Automation
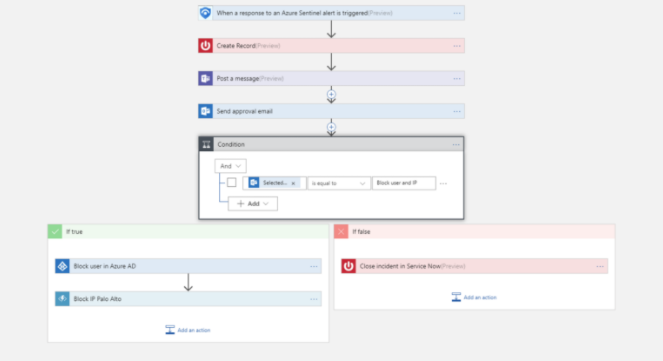
A big part of the SOC's workload is the task of triaging the numerous alerts that come in. This can be done more efficiently with automation. Azure Sentinel also uses Logic Apps to make playbooks which can automate these tasks. Alerts that tend to recur can be given appropriate routine responses automatically. For example, a playbook can open a ticket and present the type of alert, and then with just a one-click approval it can trigger an automated response such as blocking an IP address or disabling a user's credentials.
Machine Learning
Once you've seen the convenience of automation, it's hard not to want to make use of machine learning too. Microsoft says that machine learning "is at the heart of what makes Azure Sentinel a game-changer in the SOC." Azure Sentinel makes particular use of three machine learning "pillars":
- Fusion. This technology uses scalable algorithms to take millions of low-fidelity anomalies and reduce them to the most important high-fidelity incidents. It can also look at multiple activities in different kill-chain stages to identify multi-stage attacks.
- Built-in Machine Learning. Microsoft has put years of experience with traditional machine learning methods, such as transfer learning, into Azure Sentinel's toolbox.
- "Bring Your Own" Machine Learning. For companies that have the ability to build their own machine learning models, Azure Sentinel can house those capabilities for custom ML.
With these techniques, alert fatigue can be greatly reduced, as in this example from one company over the course of a month:
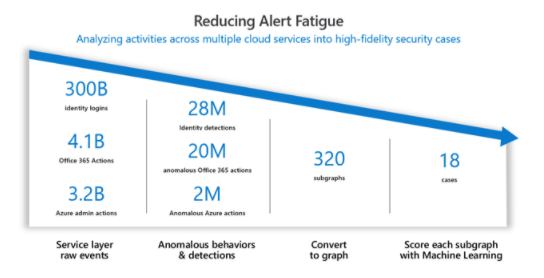
Lowering Your SOC's Alert Fatigue Will Lower Company Stress
It's always a good idea to try to reduce stress and promote well-being in your organization's employees and teams, and that goes for SOCs too. Help your security operation center team avoid burnout and stay on top of the alerts that they really need to see. By consolidating security vendors, making use of intelligence and integration, and leveraging technologies like UEBA, automation, and machine learning, you can make work more enjoyable, productive, and rewarding for this important part of your company.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Forrester Wave Gives Azure Sentinel a Leader Placement
Top 10 Security Best Practices for Azure in 2021

No Comments Yet
Let us know what you think