Top 10 Security Best Practices for Azure in 2021
Threat landscapes are constantly evolving. There are new AI & ML products on the market to address these constantly evolving threats. Let's start with the basics and make sure the front door is locked. Here are the top 10 security best practices for Azure that we deploy for every client at Infused Innovations.
1. Create a Network Security Group (NSG) to block RDP, PowerShell, and SMB from the Internet.
This should be a priority 100 rule with a source tag of the Internet. Destination ports to block are 3389, 5985, 5986, and 445 respectively. Then attach the NSG to the Virtual Network. (Don't just attach it to VM NICs as this will not cover new VMs added to the environment.) This should be your highest priority rule so that no one accidentally overrides it. These are the four most common ports that will lead to a successful ransomware attack or brute force attempt, and it's best to just block them by default.
We also suggest using a deny-first policy for Network Security Groups by using Application Security Groups (ASG) to define access. For example, if an engineer creates a new VM, and does not assign an ASG to that VM, then it is blocked by default from accessing other resources on your network. This will force new hires or contractors to adhere to your network security policies by default.
2. Enable the Azure Security Center Standard Tier.

ASC is roughly $15/mo/node (it's billed hourly) plus some additional costs for Azure SQL PaaS instances and Storage Blobs. Benefits include continuous CVE scanning, real-time threat protection, Microsoft Defender ATP licensing, and Azure CIS compliance benchmarking. Basically, Azure Security will tell you exactly what you need to enable to stay secured. Beware though, Azure DDoS standard protection and Azure Firewall both start at $900/mo minimum. Bonus: announced at Microsoft Build 2020, the Qualys CVE scanner has been added to ACS for no additional cost.
It's important to note that while continuous CVE scanning is helpful, you should have a CVE remediation plan that includes remediating all critical and high priority alerts within 30 days of discovery. All medium and low level alerts with known exploits should be addressed within 90 days.
3. Turn on Azure Sentinel.
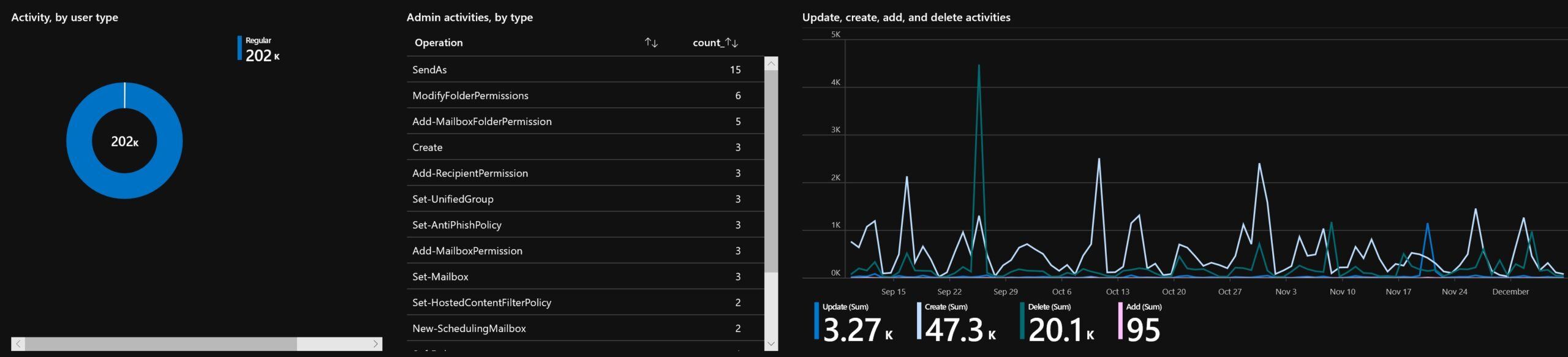
Pricing for Azure Sentinel is a little complicated. Once you get past the free tiers, it's roughly $5/GB depending on the datacenter you're in. However, all of your Microsoft 365 security logs are ingested for free and it provides a central management pane for all of your cloud security alerts. If you haven't yet, take a look at our step-by-step guide to setup Azure Sentinel.
4. Use RBAC and a Separate Admin Account.
If you're using your desktop email account as a global admin, stop reading this article right now and go create new account "admin.name@contoso.com", then setup MFA, and then transfer all your privileged permissions to this new account. Regarding RBAC--make a new user or contractor justify why they need Global Admin permissions. Your tenant should have fewer than 5 Global Admins. About half of our client projects can be completed with just the Security Administrator role.
5. Enable Conditional Access with MFA for Admin Accounts and Admin Portals.
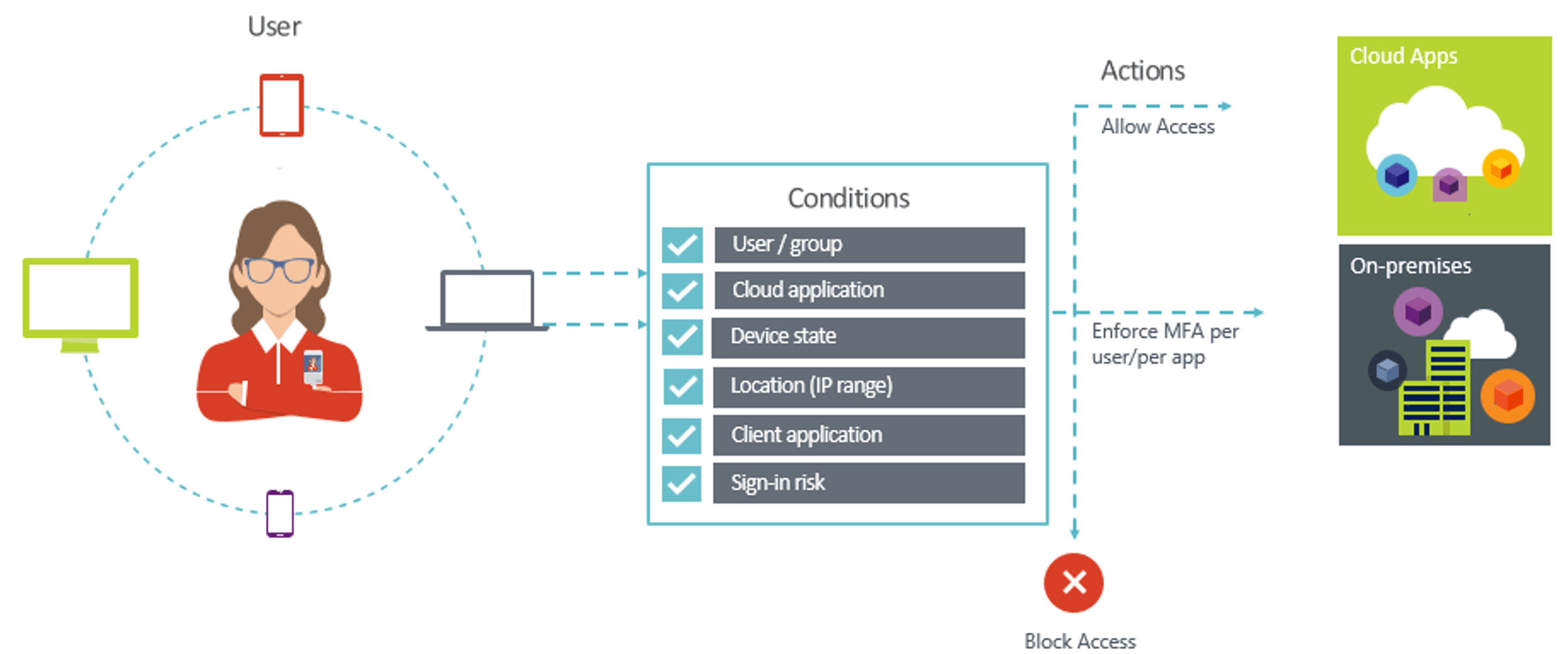
Number 5 on our top 10 Security Best Practices for Azure, but #1 in our guide for protecting Microsoft 365 is enabling MFA. At Infused Innovations, we use a belt and suspenders approach to protect Azure management portals. The first Conditional Access (CA) rule we create targets all Built-in roles that contain the word "admin" to require MFA on every login. The second CA rule targets all users, but only targets the Azure Management and Microsoft 365 management portals. This second rule is important if your organization creates their own RBAC rules with custom-named security groups.
6. Restrict Security Registration to Known IP Addresses.
After you finish onboarding your current users to Azure MFA, create a conditional access rule that restricts users from enrolling for MFA outside of your office. New remote hires/contractors will need to be exempted from the rule during onboarding, but the this exemption should be removed as soon as the user is registered.
7. Enforce Privileged Identity Management for Just-in-Time Access.
There should be no standing admin access in your environment. There is no reasonable justification for someone to have Global Admin access 100% of the time. By using a change control process--sometimes referred to as a Change Advisory Board or CAB--you can review all changes and rollback procedures prior to implementation. The change process also allows you to approve periods of time that employees may request and elevate to an admin role. For instance, in Star Wars VII, Phasma would not have been allowed to lower the shields at Starkiller base without first requesting a change window from the CAB. (You would think this change window would be denied.)
8. Use a Privileged Access Workstation (PAW) with Azure Bastion or WVD for all admin activities.
You use email and a web browser on your every day desktop. These are literally the two main attack vectors for breaches. Don't perform admin activities on the same machine that you use to read your email. Instead, log into a hardened VM running in Azure that is compliant with ASC recommendations. This VM is commonly referred to as a PAW because it's only used for privileged activities. By adopting this technique, you can create security alarms to flag admin activity from non-PAW devices to identify breaches sooner.
Azure Bastion provides a built-in remote access solution, however it has limited client capabilities. By using a Windows Virtual Desktop (WVD) instance, you can allow secure access to your environment from any device.
9. Use a Web Application Firewall (WAF) with Azure Traffic Manager (ATM).
Protecting your admin accounts is paramount, but this blog is about th Top 10 Security Best Practices for Azure infrastructure. Azure's WAF service is built on top of the Application Gateway service and prevents OWASP 3.0 attacks against SQL databases. If your web-app is not international, then lock it down with Azure Traffic Manager by using a geo-location filter. By configuring your WAF to only accept traffic from ATM, you can block international traffic, further reducing your attack surface.
10. Review Security Logs at Least Weekly.
Ingesting logs at scale can be expensive. One of the worst things you can do is pay for enterprise-grade security, have all the logging enabled for the entire attack-chain, and then completely ignore the alerts. If you don't train the AI/ML models in any of the Azure / Microsoft 365 security tools, you're going to be overwhelmed with noise, and you're going to miss a breach. Make sure you review your logs and dashboards at least once a week for any unusual behavior. Setup email/SMS alerts for high priority alerts too.
Closing Thoughts on the Top 10 Security Best Practices for Azure in 2020
Some of the suggestions above may be overkill for smaller organizations. But if you implement all of these policies, you can eliminate many of your common attack vectors. Some studies suggest that simply enforcing MFA can prevent 99% of breaches. With infrastructure, it's also important to continuously monitor your services for new exploits and persistent threats.
We're proud to offer enterprise-grade security to our local non-profits and SMBs at affordable rates. Enterprise customers can reach us via your Microsoft account executive. All customers can leave us a comment or submit a contact form below if you have any questions!
Be sure to also check out our Top 10 Security Best Practices for Microsoft 365.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts

Windows Virtual Desktop is now Azure Virtual Desktop (AVD)

Microsoft Defender for Endpoint and Intel TDT Combine for a New Ransomware Defense

No Comments Yet
Let us know what you think