Make the Most of Microsoft Threat and Vulnerability Management (TVM) by Automating with Intune
Let's say you just bought and deployed Microsoft Defender for Endpoint (MDE) to use as part of your Extended Detection and Response (XDR) service. Or maybe you got the E5 Security license for its cross-domain capabilities. You’re taking a look through security.microsoft.com to check out the possibilities and you stumble on the Threat and Vulnerability Management (TVM) section. Whoa---you already have 200+ recommendations. What does TVM cover, and where do you start? Here's a look at what Microsoft Threat and Vulnerability Management does, and a good answer to the question of how to start using it.
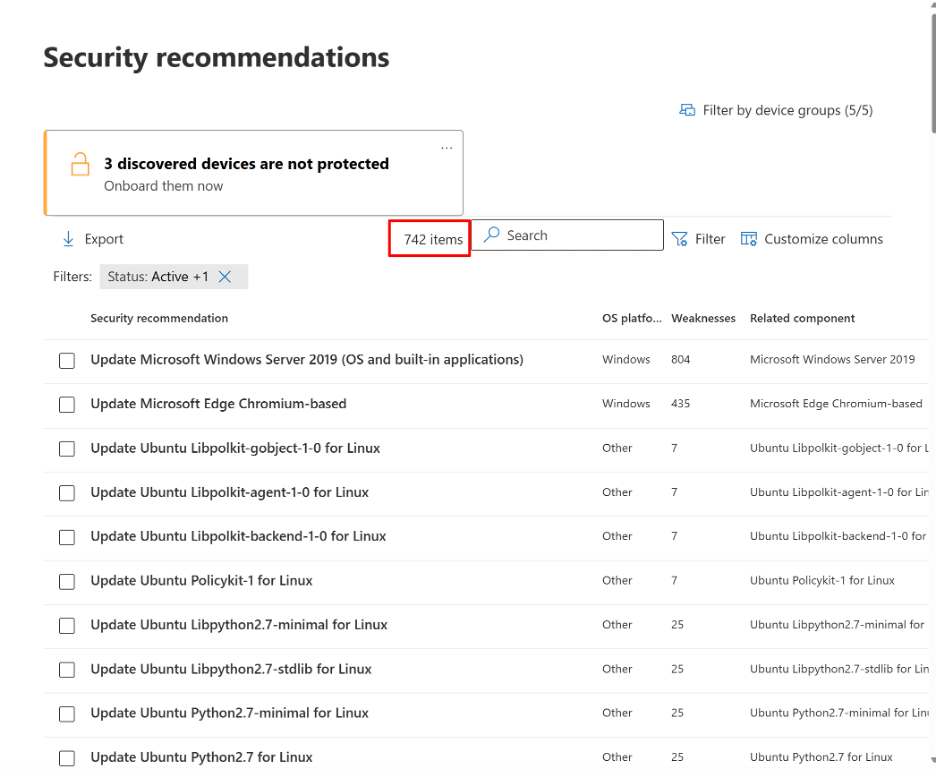
Why Use Microsoft Defender for Endpoint (MDE) Threat and Vulnerability Management (TVM)?
Microsoft Threat and Vulnerability Management is an answer to the current security threat landscape, which is more complex than ever with new vulnerabilities and attacks emerging daily. According to industry analysts such as Gartner, Forrester, and International Data Corporation (IDC), the top threats facing enterprises today include:
- Advanced persistent threats (APTs)
- Ransomware attacks
- Phishing and social engineering
- Malware and viruses
- Insider threats
By using Microsoft Defender for Endpoint's Threat and Vulnerability Management solution, organizations can proactively identify and remediate these threats, helping to ensure the security of their devices and data. The solution provides a comprehensive view of the organization's security posture, including the identification of vulnerabilities and misconfigurations, as well as the ability to prioritize remediation efforts based on risk.
Some key features of Microsoft Defender for Endpoint's Threat and Vulnerability Management solution include:
- Vulnerability assessment: This feature provides organizations with a detailed view of their security posture, including the identification of missing patches, misconfigured systems, and potential security risks.
- Exploit protection: This helps to prevent attacks by blocking malicious actors from exploiting known vulnerabilities.
- Threat and vulnerability prioritization: With this feature, organizations can prioritize remediation efforts based on the risk associated with each vulnerability or threat, helping to ensure that the most critical issues are addressed first.
- Automated remediation: Administrators can automate the remediation process, allowing organizations to resolve vulnerabilities and misconfigurations quickly and effectively.
For more details about MDE TVM, see the Microsoft Defender for Endpoint website.
How do you Operationalize a Threat and Vulnerability Management (TVM) Program?
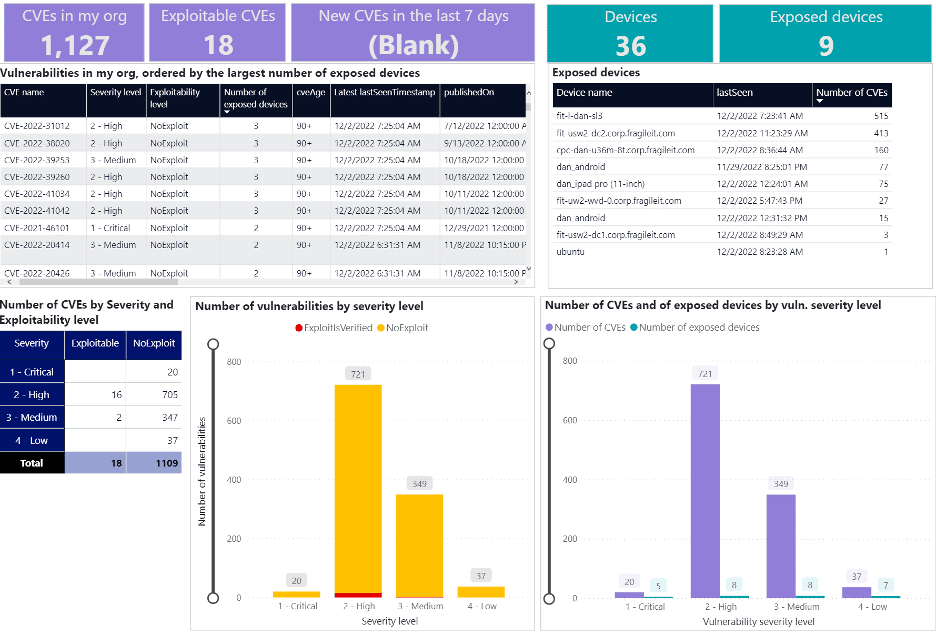
The first step you want to do is identify all the Common Vulnerabilities and Exposures (CVEs) in your environment. Once you’ve discovered these, you typically start with the ones that have known exploits available in the wild, the highest Common Vulnerability Scoring System (CVSS) scores, and the biggest impact on the most devices in your environment. After identifying which CVEs to focus on, you start assigning remediation tasks to the infrastructure teams that are responsible for the devices with each CVE.
(At Infused Innovations, we like to use Power BI to help create reports for the different infrastructure teams. Here’s a great sample report that you can use in your environment.)
New vulnerabilities, except for Zero-days, often have a 30-day grace period to be patched before your compliance team will mark a device as failing a compliance audit. We typically suggest running your patching and CVE scan reports around the sixth day of each month, which should give you at least three weeks to roll out any Windows updates from the previous month.
Automating TVM Configuration Baselines with Intune
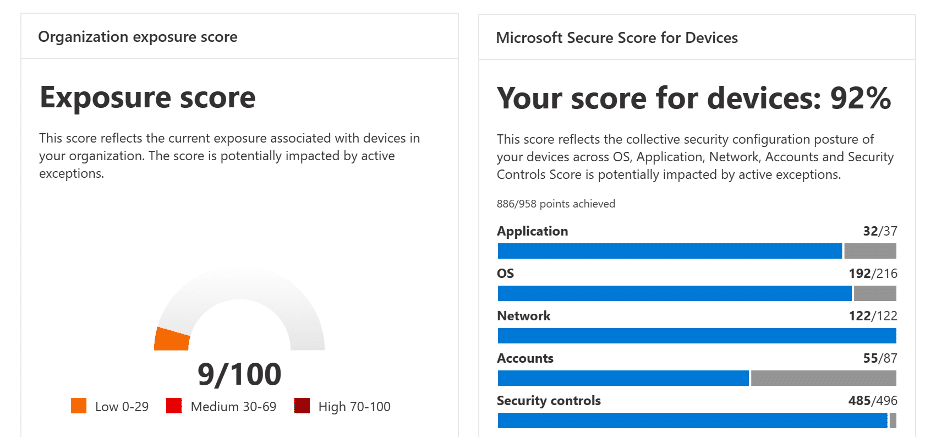
The next step which will save you a lot of trouble is to automate your configuration baselines using Microsoft Intune. If you haven’t completed any device hardening initiatives yet, your device Exposure Score in MDE TVM is probably 40+/100. While the MDE TVM module provides detailed instructions on how to remediate device misconfigurations, there are probably over 100+ recommendations in your tenant. So where should you start?
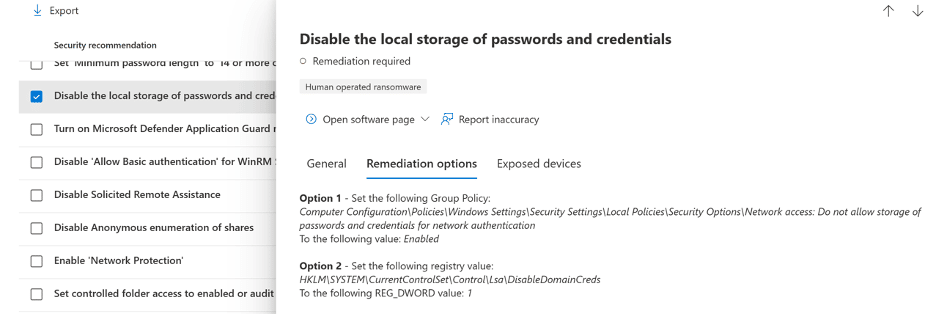
Here’s a simple answer that automation enables: start with all of them. Our former CISO, Dan Chemistruck, now works at Microsoft and has just published a GitHub repo with baselines that address 100+ device configuration recommendations in TVM. On the repository page you'll also find an open-source PowerShell tool available to import all of the JSON files into your tenant. (Keep in mind that Microsoft does not officially support these baselines, but our customers our welcome to contact us for guidance on how to implement them.)
Instructions on how to import the baselines are available in the GitHub repo, and they address recommendations for Windows 10/11 and macOS 10.15 and newer.
So once you've done the TVM reporting and baseline configurations, what’s next?
Patching: a Core Part of TVM Programs
After applying the baseline configurations above, the remaining TVM recommendations will likely be software update recommendations. Patching is always an important part of maintaining good security. Microsoft Intune released a great new feature last year called Windows Autopatch, which helps streamline your Windows updates.
If you choose to do third-party patching, using tools like Chocolatey or Winget for package management and distribution can save your IT team countless hours every month. Feel free to reach out to us if you want to learn more about how Infused Innovations uses Winget for third-party patching.
Closing Thoughts on Using Microsoft Defender for Endpoint (MDE) for Threat and Vulnerability Management (TVM)
Managing Windows updates every month is difficult enough. Staying current on remediating new vulnerabilities is critical to keeping your organization secure, but it's also a distraction from focusing on growing your business. We offer managed security services built on the Microsoft Defender XDR + Sentinel stack to help you focus on your customers while we help keep their data secure. Contact us to find out how we can help!

This article was written with assistance from ChatGPT.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Go Passwordless With Microsoft 365

A Step in the Evolution of Human-Machine Relationships

No Comments Yet
Let us know what you think