Microsoft 365 XDR
Disclaimer: It's not actually called Microsoft 365 XDR. (But a lot of people like to type that into a search engine.) MD XDR encompasses the entire security suite while the M365 security suite is referred to as Microsoft 365 Defender. We agree with you--it's just as confusing as the prior ATP product names.
Extended Detection and Response, or XDR, is becoming more relevant in counteracting increasingly sophisticated cyber threats. Key to XDR's strength is its integration across different areas of security need. Past security solutions have generally focused on these areas individually---email, for instance, or user devices. But with many different areas to keep track of, cyber attackers can sneak in between them when they're monitored separately like that. And once they've snuck in, they can spread more easily and do a lot of damage. That's why security providers are working to create the strongest and most effective XDR solutions they can. In a recent blog post, we outlined several of these XDR providers. Not surprisingly, Microsoft is one of them and offers the most extensive coverage across each security domain. Here we'll take a closer look at the Microsoft 365 XDR offering.
Microsoft Defender XDR
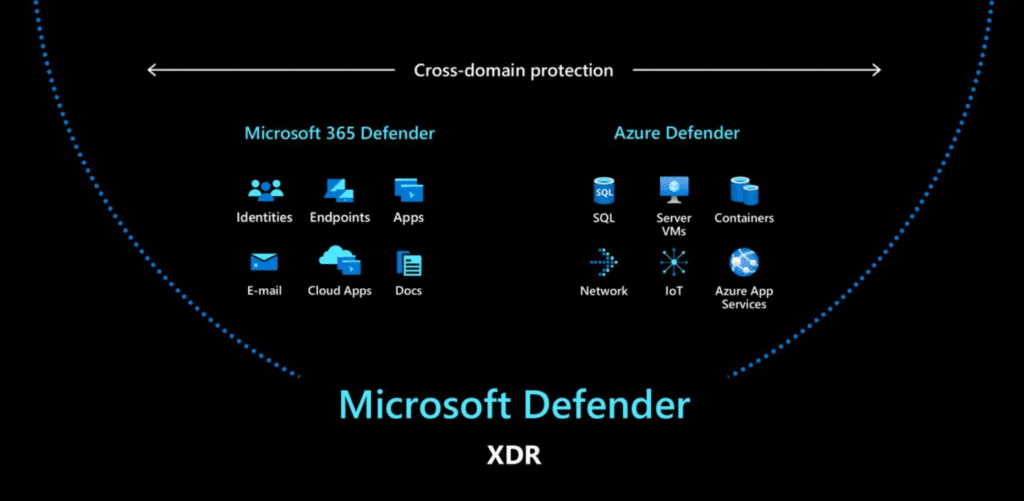
Microsoft's XDR solution breaks down into two security packages: Microsoft 365 Defender and Azure Defender. There is no license called "Microsoft Defender XDR" so you enable the XDR feature set by licensing each of the products within the suite. Together, they encompass all of an organization's security areas, with integrated threat detection. Broadly speaking, you can call the total of this cross-domain protection Microsoft Defender XDR.
Microsoft 365 Defender

The areas covered by Microsoft 365 Defender are some of the places that are traditionally very vulnerable to cyberattacks. Different Microsoft 365 licenses provide different features and their corresponding security tools; the E5 license covers all of the areas on the left side of the chart above. Some of these include:
- Endpoints. This is the realm of Endpoint Detection and Response (EDR). Nearly 70% of breaches occur at endpoints, or user devices. XDR monitors endpoints closely, tracking both Indicators of Attack (IOAs) and Indicators of Compromise (IOCs). It can identify the origin of an attack and document how it has spread along endpoints. Only an XDR solution allows for quick identification and remediation across the entire attack chain.
- Identities. Hackers love passwords. If an attacker gets access to your account, XDR uses behavior analytics to detect abnormal activity. By using machine learning to create behavioral profiles for each of your users, fraudulent activity can be detected when irregular events start appearing in event logs. For instance, if a user that typically accesses fewer than 50 files per day starts accessing thousands of files and the same user recently had a malicious email removed after delivery, then your XDR solution would correlate and create a high priority alarm for this incident. This is one example of the cross-layered nature of XDR that gives it such a strong security edge.
- Email. Yet another notorious place breaches occur is email. There are other solutions that can protect email well, but XDR's ability to correlate malicious email attacks with other suspicious activity on your network or in your cloud provides more precise information about the nature of a threat or attack. For example, instead of just blocking malicious email, XDR can identify successful phishing campaigns with suspicious data access, and many times block and data from being exfiltrated.
Azure Defender
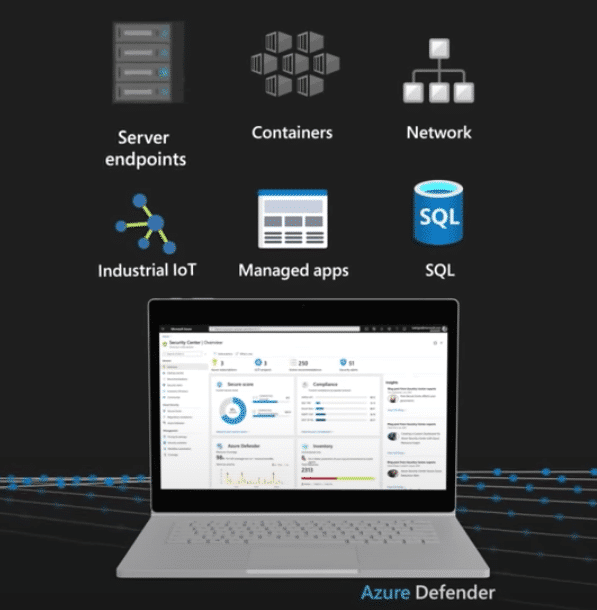
Azure Defender is especially helpful for cloud and hybrid environments. XDR capabilities can be accessed within the Azure Security Center, which provides the foundation for the offering. Some of the areas that benefit from XDR in Azure Defender are:
- Network. A lot of activity goes on through networks, so XDR's monitoring here allows for quick detection and response. Any suspicious findings are researched and tracked in their movement. Attacks can be quickly stopped, and the information gained can be used to keep track of vulnerable points in the network.
- Internet of Things (IoT). Microsoft's acquisition of CyberX last year extended its range of IoT protection and visibility. Here XDR can digitally map and assess thousands of IoT devices, finding and mitigating risk at all of those sites.
- Containers. For those using container workloads, Azure Defender's XDR provides boosted protection. This includes continuous container image tracking and stronger policy management for Kubernetes.
More on Microsoft 365 XDR
For more specifics about these features, technologies, and Microsoft's infamous branding changes regarding them, see their blog post on the unification of SIEM and XDR for security operations.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Microsoft Defender for Mobile Endpoints

No Comments Yet
Let us know what you think