Threat Hunting with Azure AD Premium Subscriptions
Every cloud security workshop that I perform with a client to enable Microsoft’s Enterprise Mobility + Security (EM+S) suite typically yields an unpleasant surprise. I had the CFO of one company demand the immediate implementation of Roles Based Access Control (RBAC) after seeing the granularity of the audit capabilities of Cloud App Security. During my most recent workshop with a national client that has 25+ offices across the US, we uncovered a large amount of Tor traffic within 15 minutes of our first session threat hunting with Azure AD Identity Protection.
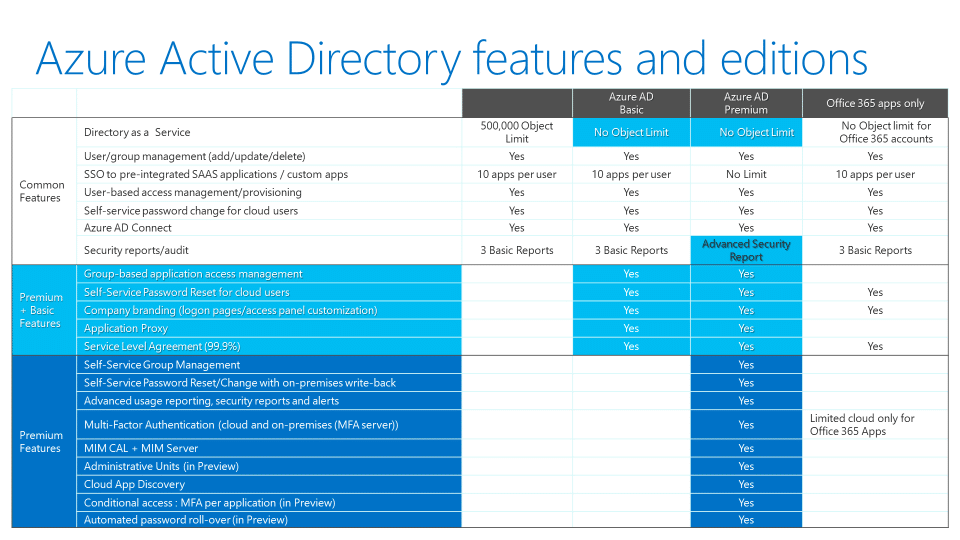
What is Azure AD Premium?
Let me start off by stating that I think every organization that cares about protecting their data should be on Azure AD P2 as either an add-on subscription or part of a Microsoft 365 bundle. Especially if you’re a small business without a 24/7 support team.
Azure AD has three SKUs:
- AAD Basic
- AAD P1
- AAD P2
Azure AD Basic comes with every Office 365 subscription and is the default SKU for all your users. Azure AD P1 provides additional reporting into identity breaches, but the responsibility is on you to audit and respond to these reports. The key benefits to Azure AD P2 are risk-based conditional access and Azure AD Identity Protection.
With the exponential increase of phishing and password spray attacks over the past year, you must automate security responses to keep up with the sophistication of modern cyberattacks, which requires AAD P2.
For a full feature comparison of Azure Active Directory, refer to the chart below. (Or follow this link for the most recent feature list)
Threat Prevention with Azure AD: Enabling AAD Identity Protection
This one feature allows me to feel comfortable going to sleep at night. Azure AD Identity Protection is available in the Azure Marketplace and uses machine learning along with artificial intelligence to review log data from your entire organization. Continuous monitoring of both Azure AD and on-premises AD environments creates risk profiles for your users to automate security responses. Risk data from Windows Defender Advanced Threat Protection also contributes to determining device risk profiles.
By default, I always enable accounts with a High-Risk to force a password change:
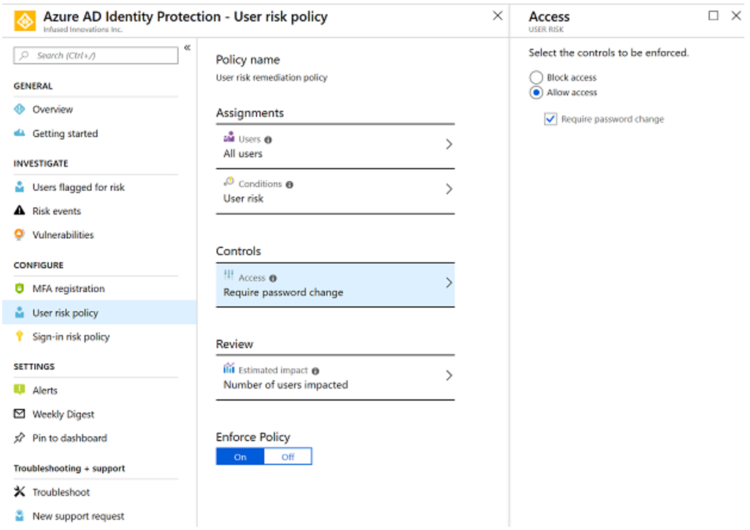
A high-risk typically indicates that the account is breached. One example is if Microsoft detects that the user’s credentials in clear text on the dark web.
For medium-level risks, I typically require an MFA challenge:
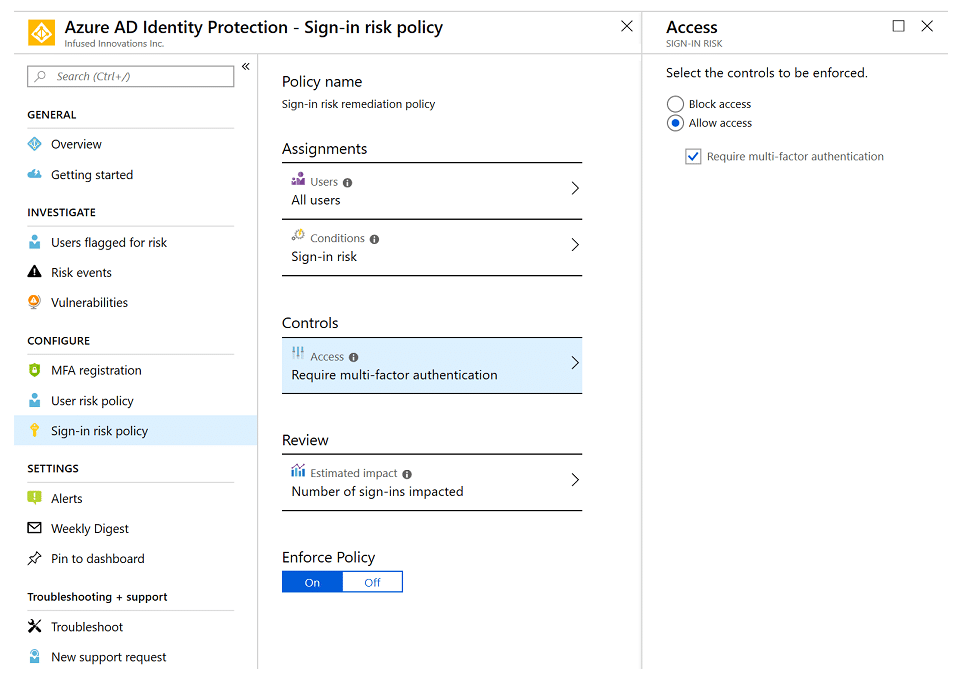
But I review the estimated impact before enforcing the policy. If there is a large potential impact, I may consider creating a conditional access policy instead. This allows for a more targeted response depending on the user activity.
Threat Hunting with Azure AD: Detecting Malicious Activity
As I mentioned earlier, I was able to identify Tor traffic within 15 minutes of activating Azure AD Premium during my last workshop. How? By reviewing the users with risky sign-ins report, we saw one user login from 9 different countries within about 90 minutes.

We responded immediately by creating conditional access policies to block countries that the company does not have business relationships with. We also require MFA challenges in other regions, including unknown regions.
I suspect Ryan was also notified by HR for violating the company’s acceptable use policy.
However, if Ryan’s credentials had been compromised, Azure AD Identity Protection would have required him to change his password immediately. No more waiting for your support desk to contact the user after determining there was a breach. The response is immediate with AAD P2.
Conclusion
I hope this has helped show the value of Azure AD P2. Automating many of the low-level tasks of a Security Operation Center using the Microsoft cloud security stack can free up your team to perform more threat hunting. We’ll explore more ways to protect your organization in our upcoming series: The Anatomy of a Breach Response.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts

No Comments Yet
Let us know what you think