Security and Productivity Don't Have to Be Opposites
Some of the most common challenges we hear from our clients have to do with a perceived battle between security and productivity. We hear CISOs saying, "I can't implement security because it makes my staff crazy / slows them down / kills their productivity." Or, alternately said, "My employees can only be productive if I let them work the way they like to work."
We understand these complaints, and we know they're based on real, everyday struggles. 74% of CISOs interviewed by Bromium said their employees were frustrated by a slowdown in productivity because of security measures. Other studies have shown even higher numbers, as well as days and days of company work lost due to efforts in security. What's causing these hindrances are often things like increased security training hours, restricted actions in applications, and blocked websites & apps. Some security measures really do slow employees down, but there are ways to improve security without doing so. Here are some tips that can help your company boost both security and productivity.
Shared File Networks
Email is a common vector for vulnerability. So, rather than employees sending each other emails with important files and information, why not send them through a shared secure network? Or don't "send" them at all -- just collaborate on the source files directly, as a team, in real-time. This way, there are less individual target points and you don't have to worry about those employees who will click on anything that gets emailed to them. Microsoft Teams is a great example of a shared hub where employees can send and store files, communicate efficiently with one another, and easily access relevant company information. After a Teams implementation, many organizations effectively pivot to an "email is external communication, Teams is internal communication" model, which is quite effective. By relegating external communications to email, employees are less likely to be tricked by the phishing attempt "from the big boss". (If you're interested, we even have a demo guide that makes it easy to set up Teams for your organization.)
Multi-Factor & Biometric Authentication
Multi-factor authentication is one of the easiest and most helpful ways to prevent accounts from getting hacked. But it doesn't have to be a headache. Oftentimes it simply requires a quick code sent to the user's phone to verify their identity (text message not recommended). An even quicker sign-in method is biometric authentication, which uses a fingerprint or facial recognition to identify the user. There are various phases of passwordless login to explore, each of which can boost both security and convenience for your employees.
Conditional Access
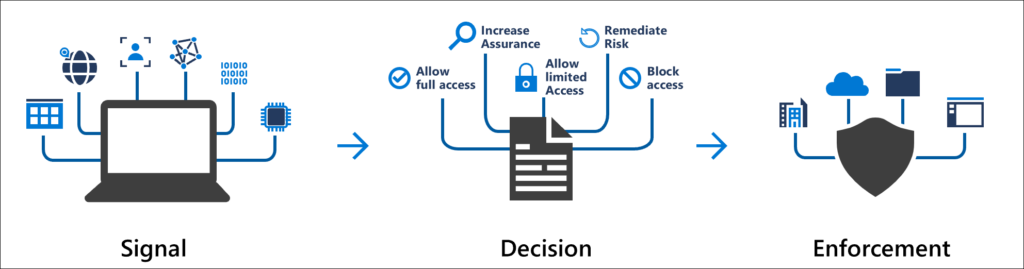
Perhaps one of the best ways to "not annoy" users with MFA challenges is by using Conditional Access. We have a detailed implementation guide on this posted, but let's talk about why it's so beneficial. Conditional Access uses various factors of an employee's sign-in (their identity, their physical location, the device their coming from, the status of their AAD account risk level, the state of endpoint software on their system, etc...) to determine in real-time whether or not to prompt the user for additional authentication.
Conditional Access policies at their simplest are if-then statements, if a user wants to access a resource, then they must complete an action. This can work with first-party Microsoft applications, as well as third-party SaaS applications that have been SSO-integrated via SAML or OAUTH against your AAD instance.
By using Conditional Access policies, you can apply the right access controls when needed to keep your organization secure and stay out of your user's way when not needed.
Automated Password Managers

Automation is always our friend when it comes to productivity, and it can help with security too. For those who aren't ready for the biometric or passwordless login methods mentioned above, you might consider an automated password manager. The need to remember, enter in, and periodically change passwords is a common employee complaint. A password manager can generate strong passwords that employees don't even need to remember. It creates a sort of encrypted "vault" that holds all these strong, and separate, passwords for each account. The user then must remember only one password to automatically access the ones in the manager.
Role-Based Access Control (RBAC)
It's important to know what each of your employees needs to be able to access in order to do his or her job. Restricting necessary access will hinder productivity and bring on the complaints---but identifying and restricting unnecessary access will improve security without the employee seeing a difference in workflow. Role-based access control (RBAC) categorizes employees based on what information they need and limits their access to sensitive data that they don't need. Less access is more secure, and having a good understanding of your employees' roles will basically make this security improvement invisible to them.
Security and Productivity Can Work Together

When security and productivity are seen as opposing competitors, company leaders often prioritize productivity. It's no fun to see work get hindered, and it's a big employee complaint when they're held back. But this can create a dangerous environment and even lead to disastrous results. Moreover, it's a dichotomy that doesn't need to exist---you don't have to choose one or the other. Security and productivity can both be achieved. We're all about win-win solutions, so let us know your challenges and we'll help you boost both of these areas in your organization.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts

What's all the Hype About NFTs?
Financial Cybersecurity for Modern Hacks on World Banks
No Comments Yet
Let us know what you think