Get Your Organization Ready to Leave Passwords Behind
So many passwords, such a headache and waste of keystrokes...I'm ready to drop these things completely. Chances are, you or your employees have felt this way to one extent or another. If you are a CISO or security manager, you've probably gone even further and thought to yourself: there's got to be a more secure way. Passwords are vulnerable, as our youngest interns have demonstrated. There is a more secure way to verify identity, and it's not quite as difficult as you might expect. When you do decide to move to passwordless authentication, you'll want to make the transition as smooth as possible for your team and employees. Here's how to get your organization ready to leave passwords behind.

Create a mindset of passwordless positivity
First of all, give some consideration to how you want to present the transition to your employees. Highlighting the benefits of this change will increase enthusiasm and understanding when temporary inconveniences come up. Most employees would be happy to drop passwords since they're tedious to remember and type in. Framing the transition as a way to make their lives easier--as opposed to just another mandatory change in security practice--helps get them on board for the project.
Many of our clients have been so successful with this strategy, that they are able to use going passwordless as a "carrot" for other initiatives. For instance, "enroll your devices with Intune, and your password will never expire again." Consider eliminating password expirations as a reward for making your environment more secure.
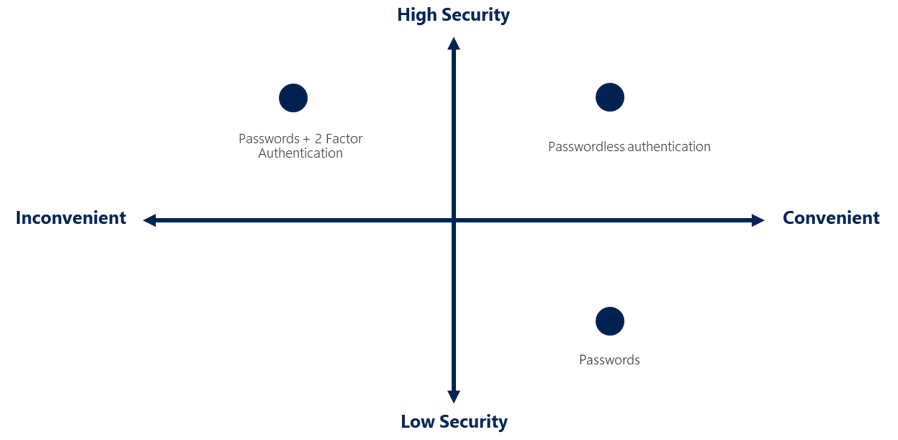
Segment your user population
You'll need to divide your users into two groups: those who are in compliance-related jobs (for example, employees who deal with payment information) and those who aren't. Some industries have compliance regulations that actually require usernames and passwords. Eventually these regulations will catch up with security technology, but until then you'll need to keep this segment of your organization using the old-fashioned passwords.
Create banned passwords
During the transition, you can strengthen the passwords employees are using in the meantime by making sure they aren't allowed to use anything easily guessable. Birthdays, sports teams, strings of consecutive numbers--you decide what's too easy to be permissible. You can also use machine learning to help you make the call and create the list. Azure Active Directory (Azure AD) password protection is an example of a tool that can aid in this job.
Modernize Hardware
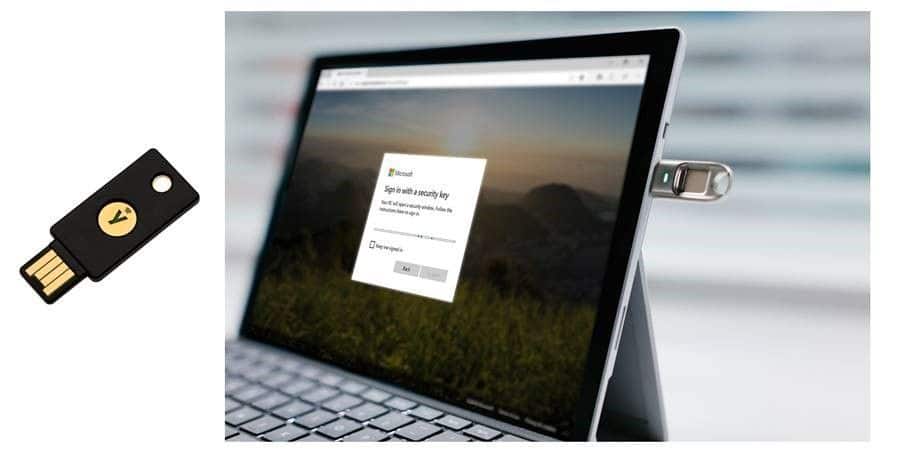
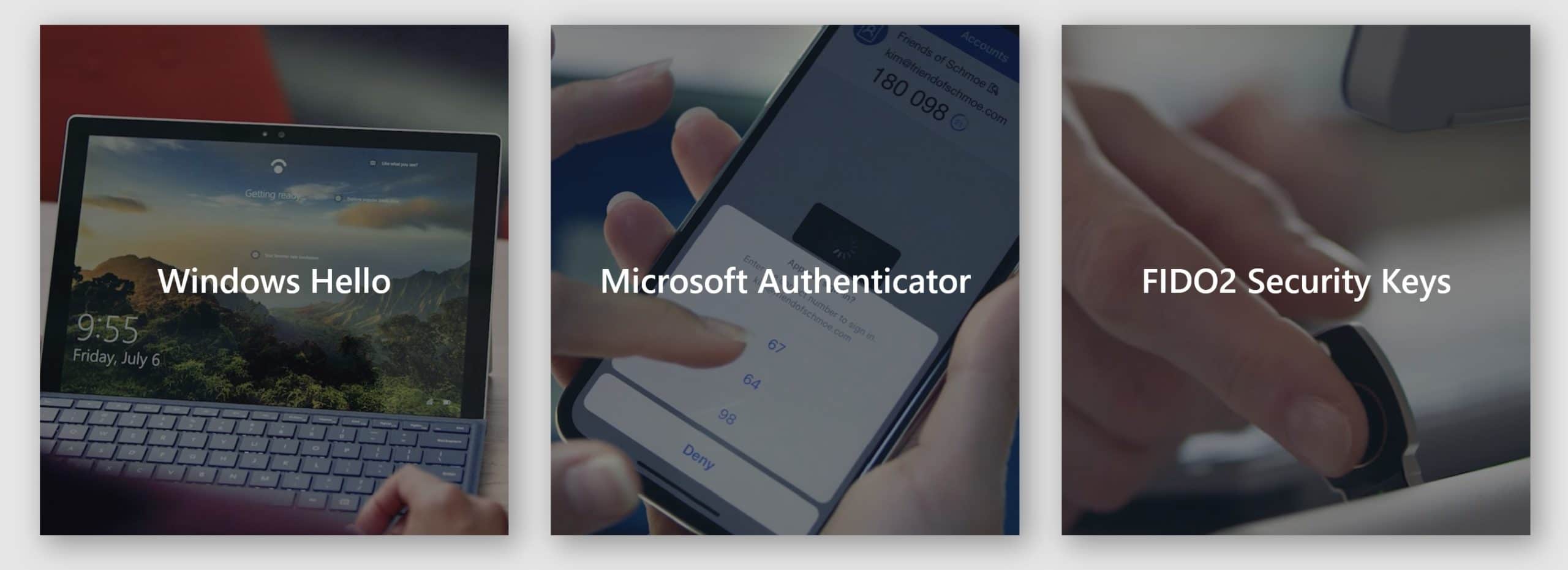
You'll want your hardware to have biometric reader capabilities and make use of Trusted Platform Module 2.0 (TPM2.0), or FIDO 2.0 and above. Other hardware options support multi-factor authentication without biometrics. These are still a big security improvement, but the new FIDO 2.0 biometric technology will provide the most seamless user experience.
Switch to multi-factor authentication
Also called two-factor authentication, this method requires two pieces of proof of a user's identity. This capability is under-utilized in organizations and is a very effective way to increase security. There are lots of options to implement MFA, such as smart cards, tokens, or FIDO keys. The public preview of Azure AD can help guide companies through MFA implementation as they move toward leaving passwords behind.
Phase-out legacy authentication
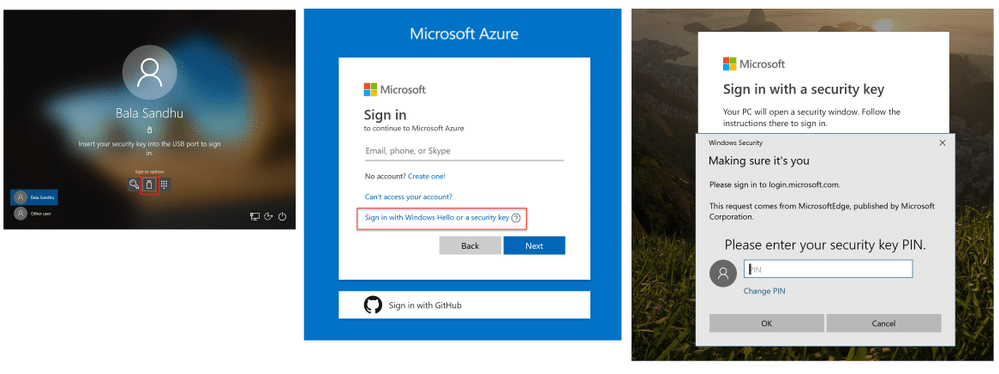
If your company has already moved completely to the cloud, great! You can skip this paragraph. For others, there will be old protocols that use basic authentication and aren't capable of enforcing any kind of second-factor authentication. It can be tedious to eliminate legacy authentication, but it needs to be done. Once again, Azure AD can help identify applications that run legacy authentication, and you can also use Conditional Access to block it.
Enable FIDO2 Authentication
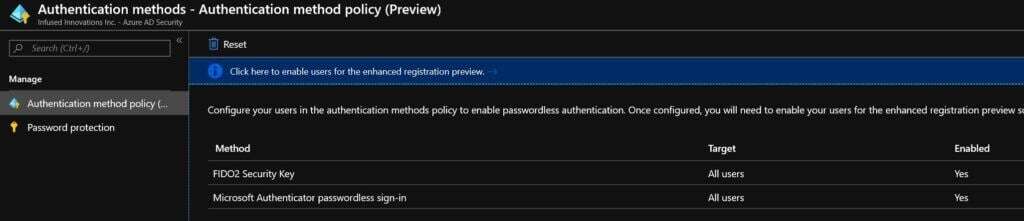
Navigate to the Authentication Methods blade in the Azure portal and enable the FIDO2 Security Key option. (Note, FIDO2 auth is currently in public preview as of December 2019.) For a list of providers that manufacture compatible FIDO2 keys, see the chart below.
| Provider | Contact |
|---|---|
| Yubico | https://www.yubico.com/support/contact/ |
| Feitian | https://www.ftsafe.com/about/Contact_Us |
| HID | https://www.hidglobal.com/contact-us |
| Ensurity | https://www.ensurity.com/contact |
| eWBM | https://www.ewbm.com/support |
| AuthenTrend | https://authentrend.com/about-us/#pg-35-3 |
Accept the journey of leaving passwords behind
Going passwordless may take a while, and that's okay. But getting your company ready for the change can start now. Any of the above steps is an improvement in security, even if they don't all happen right away. By accepting this, you can take steps as you are able and still get on the road, with passwords gradually shrinking in your rear-view mi
If you work for bank or financial organization, be sure to read about financial Cybersecurity for modern hacks on world banks.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Go Passwordless With Microsoft 365
Top 10 Security Best Practices with Microsoft 365 in 2021

No Comments Yet
Let us know what you think