Top 10 Security Best Practices with Microsoft 365 in 2021
Welcome to my initial blog post for our Secure Modern Workplace series! At Infused Innovations, one of our core security philosophies is that human minds can no longer keep up with the pace of cyberattacks. We must leverage automation through artificial intelligence to respond to security threats. With that in mind, let's look at some security best practices with Microsoft 365.
Step 1: Choose a Strong Password
Whether your IT staff is using Welcome123$ as a temporary password, or your users are trying to keep up with frequent password changes, password spray and brute force attacks will still work on at least one account in most organizations. Longer passwords are more secure, so encourage your users to string a phrase together, such as Patagonia-2019Q1-Penguin or Artichoke!0808!Heart.
Azure AD allows you to ban 1,000 custom passwords for cloud users for free. We recommend adding any common terms used in your organization or at least starting with this list of common passwords available on GitHub.
If you’re using Azure AD Connect, then you’ll need at least an AAD P1 license for each of your users. We recommend Microsoft 365 Business as a starting point for most of our customers, which also includes this feature.
Step 2: Enable Multi-Factor Authentication
Enabling Azure MFA is the number one security recommendation for all clients—just look at Microsoft Secure Score. When MFA is deployed with conditional access, your users may not even be aware that it’s enabled, as you can select a corporate-owned and compliant device as an acceptable MFA challenge.
Get used to me saying this: Azure MFA is included with Microsoft 365 Business, otherwise it requires an AAD P1 license.
Step 3: Configure Conditional Access
Does your company have employees in Russia, China, North Korea, or Nigeria? No? Then block them with conditional access.
Most organizations have login attempts from around the world and aren’t even aware of it. For example, here is a map of login attempts for a small company with less than 10 employees that only operates in the United States:
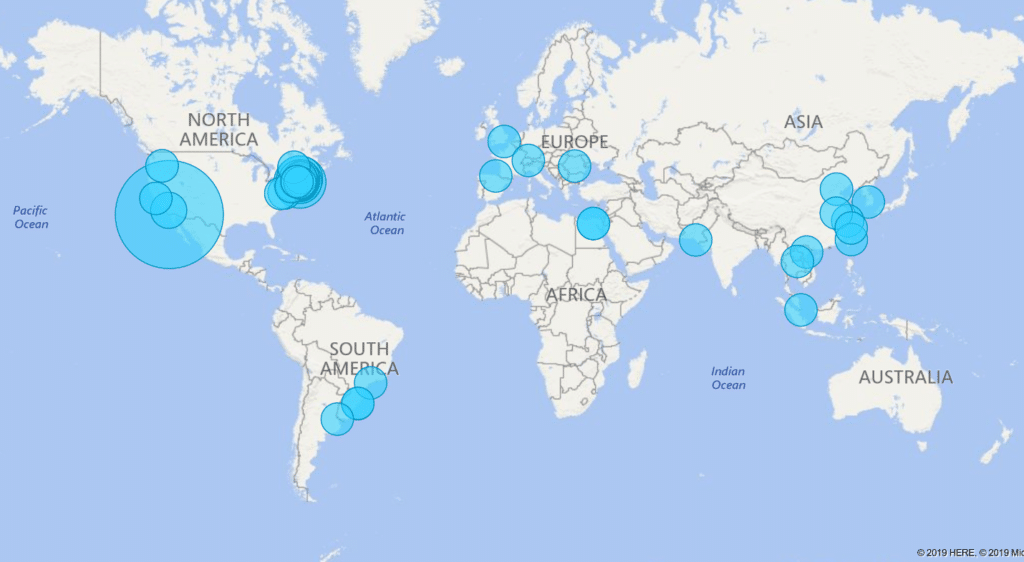
By enabling Conditional Access, we were able to block all foreign login attempts. If the CEO goes on vacation, we created a mitigating rule that she can still access her email from a company managed and compliant device.
Step 4: Use Secure Score
The new Microsoft Security Center was released this month, and will appear in your tenant soon if it hasn’t yet. Secure Score uses machine learning to help point out security best practices with Microsoft 365.
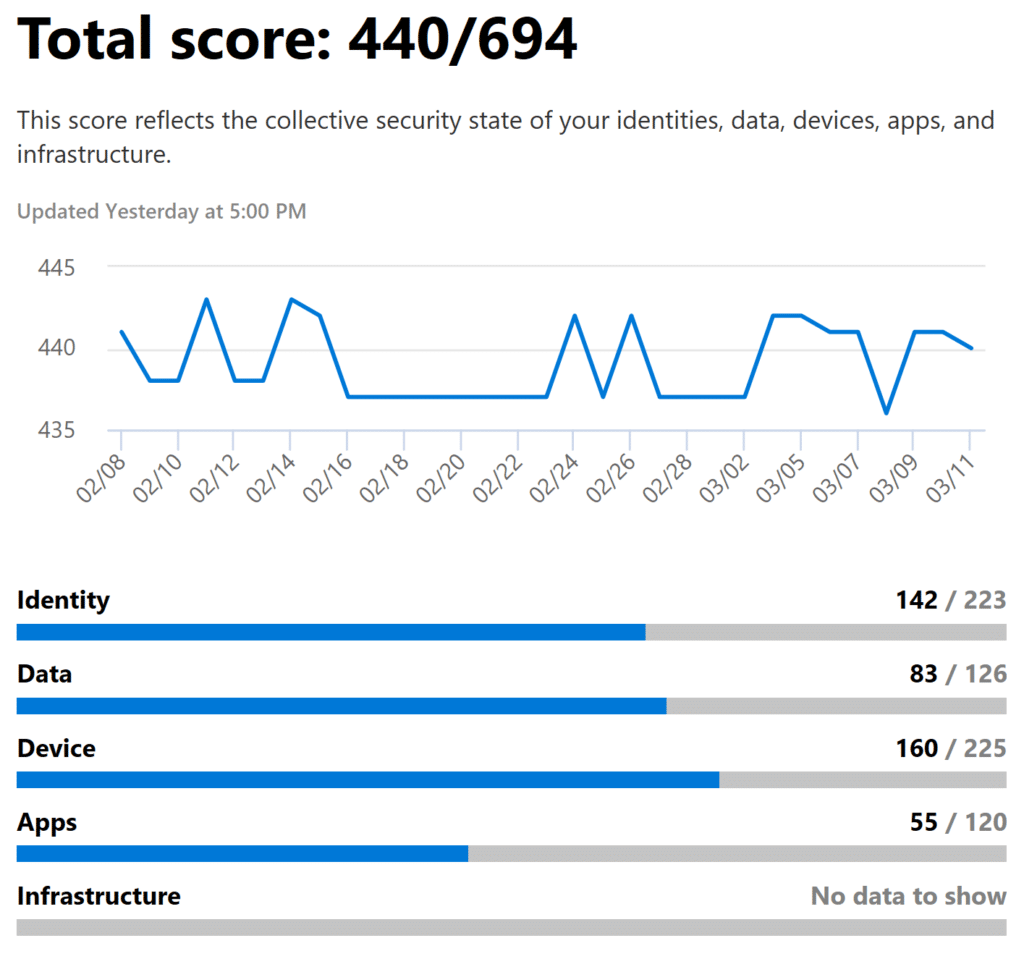
Available to all clients, use it to keep track of Microsoft recommended best practices to keep your environment secure.
If you are an Infused Intelligent Threat Protection client, we review your Secure Score quarterly and our automation engineers help to rapidly deploy new recommendations to your environment with minimal user impact.
Step 5: Secure Mail Flow
Configure Sender Policy Framework (SPF), Domain Keys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC) records. Creating a few simple DNS text records will go a long way to prevent malicious actors from spoofing your domain. Sound confusing? Infused Innovations will help you configure SPF, DKIM, and DMARC for free in our effort to make the internet a safer place. Or configure Valimail DMARC monitoring with Office 365 and Azure SSO using our step by step guide.
Infused Innovations also recommends enabling Office Advanced Threat Protect P1/P2 for all of our clients. (Also available as part of Microsoft 365 Business.) This product gives you the following benefits:
- Safe Link URL scanning for all hyperlinks in an email. Microsoft scans the website for malicious content before allowing your users to access the website.
- Safe Attachment scanning. Microsoft opens all attachments in a detonation chamber so scan for malware before delivering the attachment to your users.
- Safety Tips for suspected Phishing and Spoofing attempts.
- Anti-Malware protection and advanced reporting
Step 6: Enable Logging and Auditing
Microsoft’s Azure Sentinel is an advanced cloud-native SIEM solution that can interpret log events from your Office 365, Azure, and AWS instances.
Enabling mailbox auditing in Office 365 is free, and additional logging can be collected from Azure Active Directory for under $15/mo in many SMB/SME tenants. Some threat hunting examples using Azure AD are available here.
Additional log interpretation can done using other Microsoft cloud services, such as Cloud App Security for your SaaS and Windows 10 machines, or Azure Security Center for any Windows Server running on-premises or in the cloud.
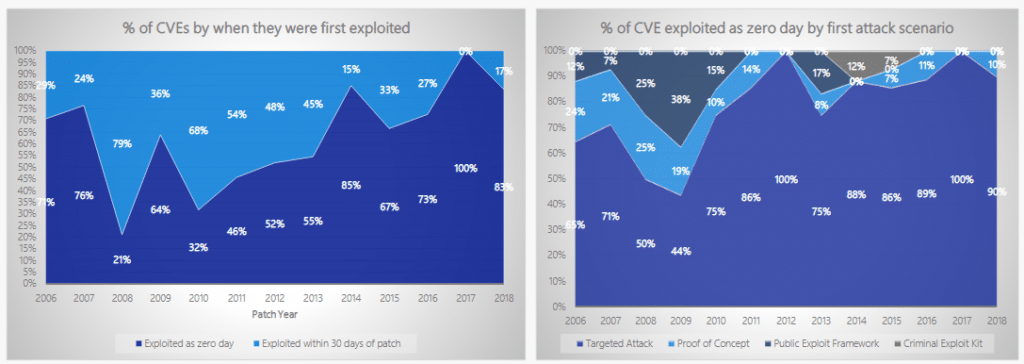
Microsoft collects over 6.5 trillion daily signals, giving them the largest dataset of any security AI vendor in the world. The days of Microsoft being a security vulnerability are over—most customers leveraging the full stack of Microsoft products will receive automated security response policies blocking a new threat within 15 minutes of the first global outbreak.
The chart above shows that in the past two years, vulnerabilities are mostly being exploited as targeted zero-day attacks and are no longer the norm.
Step 7: Use Mobile Device Management (MDM) and Mobile Application Management (MAM)
ActiveSync is allright—it lets you wipe a device if it gets lost, but it doesn’t sandbox your organization’s data, or apply advanced compliance policies.
With Microsoft Intune—a part of Microsoft 365 Business—it allows you to manage your Windows 10, iOS, and Android devices from a single location, no matter where the device is located. Anywhere in the world. Wow.
Intune allows you to define which apps on a mobile device can access corporate data, and also fully deploy your productivity suite of software to a Windows 10 device, backup the BitLocker encryption keys to Azure AD, and deploy security compliance policies. All the user has to do is log in to the device using their work account to receive the policy. It’s literally that simple.
Step 8: Turn on OneDrive Known Folder Protection
Are you still redirecting users’ desktops and documents to a file server for backups? Or worse, do you not have backups for your desktop users? Enable OneDrive Folder Protection right now to have your users backup their Desktop and Document folders to the cloud. No VPN tunneling required. No latency concerns when there’s poor internet access.
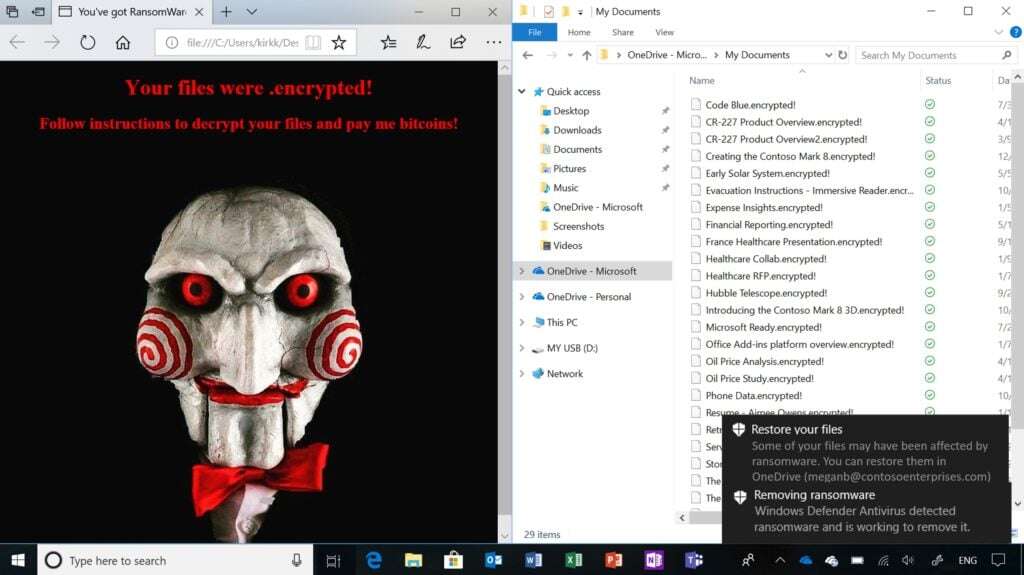
Plus, if a device gets infected with ransomware, OneDrive keeps 100 versions of every file by default, so you can just rollback the version of all your files, reimage the device, and the user is ready to keep working. (But your users won’t get ransomware, because you’re running Microsoft Defender Advanced Threat Protection alongside Windows Defender Application Guard to sandbox your browser, right?)
Step 9: Work Towards a Zero Trust Network
If you’re like me, I love my users, but I don’t trust any of them. That’s why Infused Innovations recommends a defense-in-depth security approach with a zero trust framework. Just because a user brought in their unencrypted personal laptop to the office, doesn’t mean that IT should automatically allow it to access data since it’s on the corporate network. (This wouldn’t happen because you have 802.1x authentication enabled, right?)
Or when HR is trying to email my social security number—unencrypted—to our benefits provider, even though they’re a trusted vendor, our Data Loss Prevention policies will automatically enable Office Message Encryption before the email is sent.
When security is done correctly, the same higher level of scrutiny that you require remote workers to adhere to can be used at the office too, in a way that is transparent to your users.
Step 10: Use Role Based Access Control
Our final recommendation for security best practices with Microsoft 365 is to stop logging into your email with your global admin account. Stop. Right now. Go make a separate administrator account and never use it to log into a desktop ever again. And your Service Desk administrator doesn’t need Global Admin access either, because they’re probably not paying the bills.
Review what access each of your employees need, and only grant them administrator access for that specific role. This adheres to the just-enough-access policy to make sure when an account is breached, the malicious actor does not have access to resources that were unnecessary for the employee to complete their job.
Summary of our Security Best Practices with Microsoft 365
Another core philosophy at Infused Innovations is that security tools must be easy to use. If a security initiative fails, it’s typically because it prevented a user from doing their job efficiently.
Enabling most of the features in this article will have minimal impact on your users’ everyday workflows. You may have also noticed that just about every feature in this article is included with Microsoft 365 Business.
If you’re not on a Microsoft 365 SKU yet, and you care about protecting your data, consider upgrading now. Infused Innovations is a Microsoft Gold Partner and can assist with providing a complete licensing and management solution for your organization. Don't wait to implement these security best practices with Microsoft 365— your data is at risk!
Using Azure with your Microsoft 365 subscription? Check out our top security best practices for Azure to see how you can use your M365 security licensing to protect Azure too.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
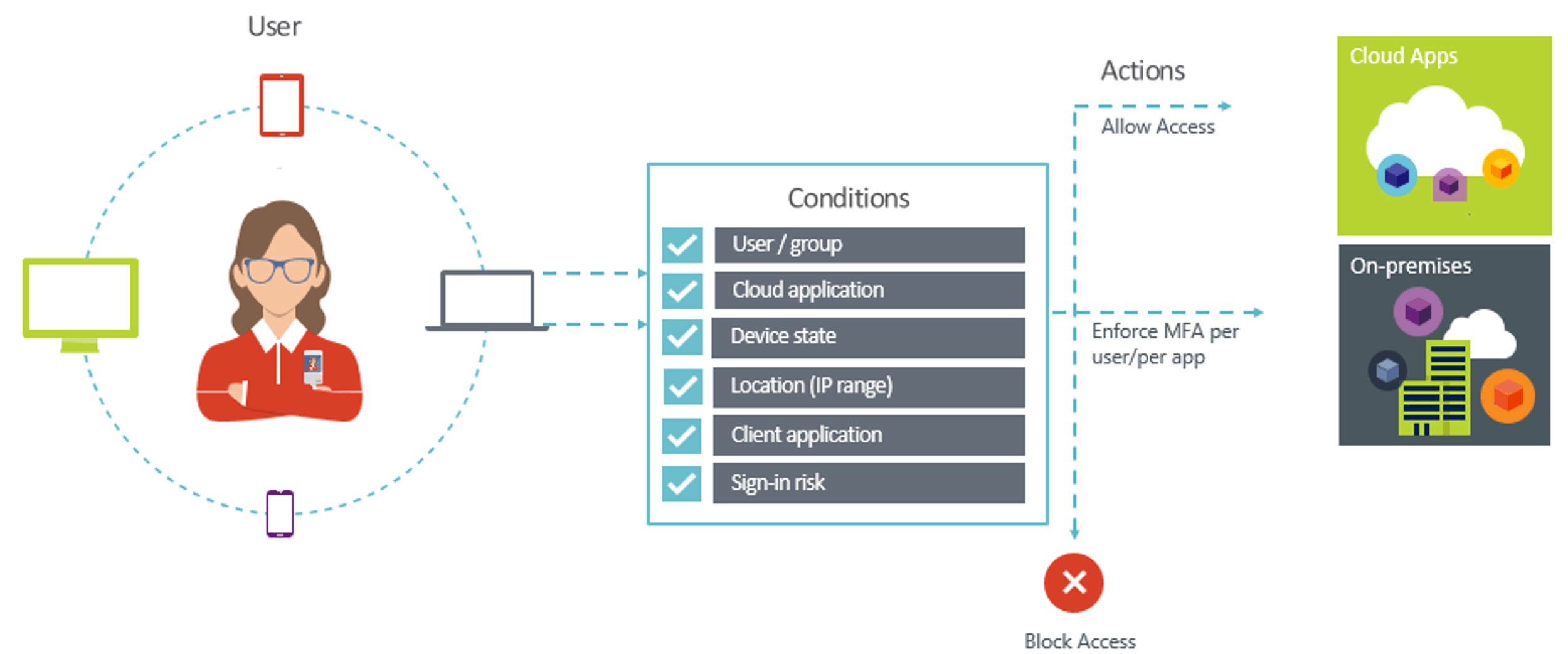
Better together: Conditional Access with Azure MFA (Multifactor Authentication)

A Zero Trust Guide for Azure AD
No Comments Yet
Let us know what you think