MITRE D3FEND and Azure Mappings: Counteracting ATT&CK Methods
MITRE D3FEND: the Counterpart to ATT&CK
If you've worked with MITRE ATT&CK, the D3FEND knowledge graph will look familiar. In a similar layout, it categorizes dozens of defense measures against various types of attacks. Across the top of the MITRE D3FEND matrix are several stages: Harden, Detect, Isolate, Deceive, and Evict. Listed down the columns are defensive processes and specific actions that can be done to achieve them (like the tactics and techniques of ATT&CK, respectively). When you click on any of the items in the matrix, you get an info page defining the term and how it works, with considerations noted as well as any digital artifact relationships or related ATT&CK techniques. Finally, references and supporting articles are listed and linked at the bottom for additional follow-up. [caption id="attachment_6620" align="aligncenter" width="1024"] Example of information about a defense method,
Connected Honeypot[/caption] This builds on MITRE's ATT&CK framework and adds to security professionals' toolkits much more thoroughly. ATT&CK was made to help defenders understand the nature of various kinds of attacks, which is an initial step toward a more informed response. Mitigation methods are included on the info pages of ATT&CK techniques, but only briefly. D3FEND expands the informational resources at security teams' disposal. They can use it to identify which defense measures they are implementing and how well. It can also help them research security measures before making choices on investments and security actions. Like ATT&CK, D3FEND is freely accessible to anyone who wants to use it---they need only
visit its website---but the fullest use of its potential is with security tools or services mapping to its matrix.
Example of information about a defense method,
Connected Honeypot[/caption] This builds on MITRE's ATT&CK framework and adds to security professionals' toolkits much more thoroughly. ATT&CK was made to help defenders understand the nature of various kinds of attacks, which is an initial step toward a more informed response. Mitigation methods are included on the info pages of ATT&CK techniques, but only briefly. D3FEND expands the informational resources at security teams' disposal. They can use it to identify which defense measures they are implementing and how well. It can also help them research security measures before making choices on investments and security actions. Like ATT&CK, D3FEND is freely accessible to anyone who wants to use it---they need only
visit its website---but the fullest use of its potential is with security tools or services mapping to its matrix.
Microsoft's ATT&CK Mappings for Azure Security Center
Also this summer, around the time MITRE D3FEND was published, Microsoft announced mappings to MITRE ATT&CK from Azure Security Center. Mappings for D3FEND should be coming soon as well, although there isn't an announcement on the date yet. The mappings linking Azure's tools to ATT&CK techniques came as part of a project by the Center for Threat-Informed Defense. This project happened in recognition of the need for teams to map their security controls to ATT&CK, as well as the difficulty for them to do that on their own. With independent security controls (as opposed to features that rely on third party products or services), Azure was chosen as the first cloud platform to be mapped to ATT&CK. This results in a better understanding for Microsoft clients about the security controls that they have in Azure Security Center, as well as a clear visualization of where they stand against the techniques that cyber attackers use. [caption id="attachment_6627" align="aligncenter" width="768"] Mappings of Azure's security controls to MITRE ATT&CK techniques, with color-coded levels of protection[/caption] The nicely colored mapping matrix shows levels of security coverage for different ATT&CK techniques. A color legend highlights which areas are most protected and where bigger vulnerabilities lie. This is helpful in assessing risks and also for testing and developing stronger defenses.
Mappings of Azure's security controls to MITRE ATT&CK techniques, with color-coded levels of protection[/caption] The nicely colored mapping matrix shows levels of security coverage for different ATT&CK techniques. A color legend highlights which areas are most protected and where bigger vulnerabilities lie. This is helpful in assessing risks and also for testing and developing stronger defenses.

More About MITRE D3FEND
MITRE ATT&CK and D3FEND both give cybersecurity teams clarity and resources to better strengthen their organizations. Any built-in mappings to them only make the process that much more workable. D3FEND is still relatively new and MITRE plans to continually build on it, and we can look forward to the ways Microsoft and other security companies link their technologies to it as well. For now, you can read more in-depth about how D3FEND was developed in MITRE's technical report on it. More of our recent blogs:Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
What is MITRE ATT&CK?
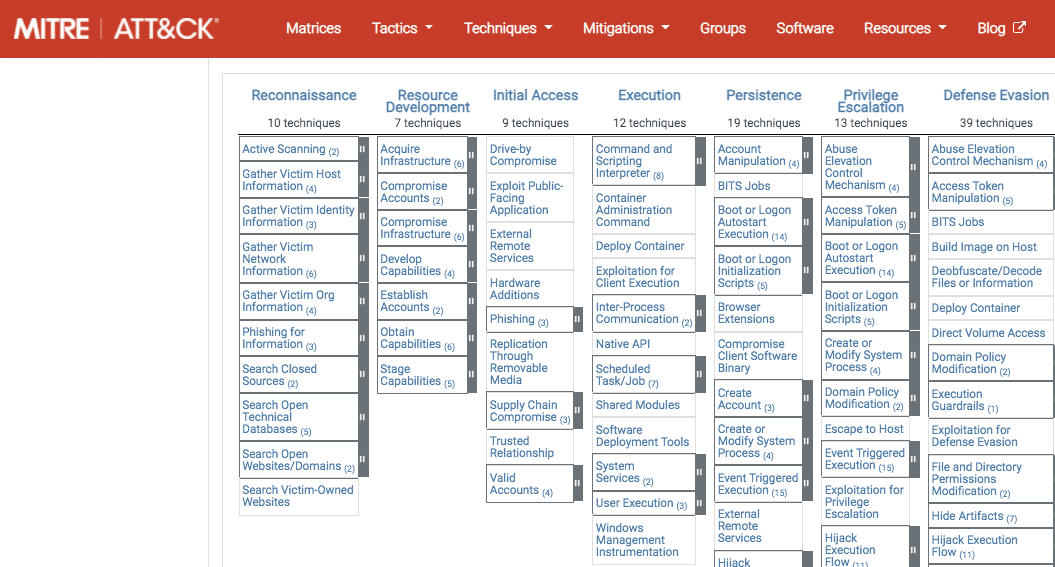

What is MITRE ATT&CK?
October 18, 2021
3
min read
What is Content Disarm and Reconstruction (CDR)?


What is Content Disarm and Reconstruction (CDR)?
June 21, 2021
3
min read
Microsoft Defender for Endpoint and Intel TDT Combine for a New Ransomware Defense


Microsoft Defender for Endpoint and Intel TDT Combine for a New Ransomware Defense
March 14, 2022
3
min read
No Comments Yet
Let us know what you think