Easily Moving from CrowdStrike to Microsoft Defender for Endpoint
Whether your organization is looking to move off CrowdStrike Falcon due to the July 2024 incident, or you are trying to better leverage your organization's investment in Microsoft 365 with the Defender for Endpoint P2 license, or you're simply looking to improve your organization's security posture from a lesser product current deployed, the adoption and enablement of Microsoft Defender for Endpoint has never been easier!
Why Businesses Should Consider Moving from CrowdStrike to Microsoft Defender for Endpoint
First, let's back up. The recent disruptive incident involving a CrowdStrike Falcon driver update, which resulted in boot loops and blue screens of death on millions of endpoints, underscores the critical need for robust and reliable cybersecurity solutions. Whether your organization was disrupted or not, having an endpoint security product deployed that respects categorical update rings is critical. The recent CrowdStrike event not only led to significant downtime but also impacted the global economy, highlighting the vulnerabilities associated with dependency on a single cybersecurity provider that may have sub-standard DevSecOps and/or QA practices.
In light of these challenges, it is crucial for businesses to explore alternative solutions that offer better stability and control over updates. One such solution is Microsoft Defender for Endpoint, which provides comprehensive security features along with robust support for update rings across categories.
Understanding Update Rings in Microsoft Defender for Endpoint
Update rings are a pivotal feature of Microsoft Defender for Endpoint that allow businesses to have granular control over how updates are rolled out across their environments. This mechanism ensures that updates can be deployed in a staged manner, starting from a small group of test devices, which can then be expanded to include more devices based on the success of initial deployments. This phased approach helps in identifying any potential issues early in the deployment process without affecting the entire network, thereby minimizing disruptions.
Advantages of Switching to Microsoft Defender for Endpoint
-
Enhanced Stability and Reliability: By using update rings, businesses can ensure that only thoroughly tested updates are deployed across their critical systems. This reduces the risk of encountering fatal errors that can lead to system downtimes, as seen in the recent Crowdstrike incident.
-
Integrated Security Solution: Microsoft Defender for Endpoint is seamlessly integrated with other Microsoft products and services, providing a unified security posture that is easier to manage and scale. This integration helps in leveraging the robust security frameworks of Microsoft, which are backed by extensive research and regular updates.
-
Advanced Threat Protection: Apart from managing updates efficiently, Microsoft Defender for Endpoint offers advanced threat protection capabilities including endpoint detection and response (EDR), automated investigation and remediation, and threat vulnerability management. These features provide an added layer of security by actively detecting and mitigating potential threats in real-time.
-
Scalability and Flexibility: The solution is designed to cater to businesses of all sizes, offering flexibility in terms of deployment and management. Companies can scale their security measures as they grow, adapting to new challenges without needing to switch providers.
Simplifying Setup with GitHub Repository
To aid businesses in transitioning to Microsoft Defender for Endpoint, Microsoft employees have provided a comprehensive repository on GitHub, which can be found here: MDE-Rapid-Configuration. This repository includes scripts and documentation that simplify the setup process, making it easier for businesses to onboard quickly and efficiently. The resources available in this repository help in automating many of the initial setup tasks, reducing the technical barrier for businesses looking to switch their endpoint security solution.
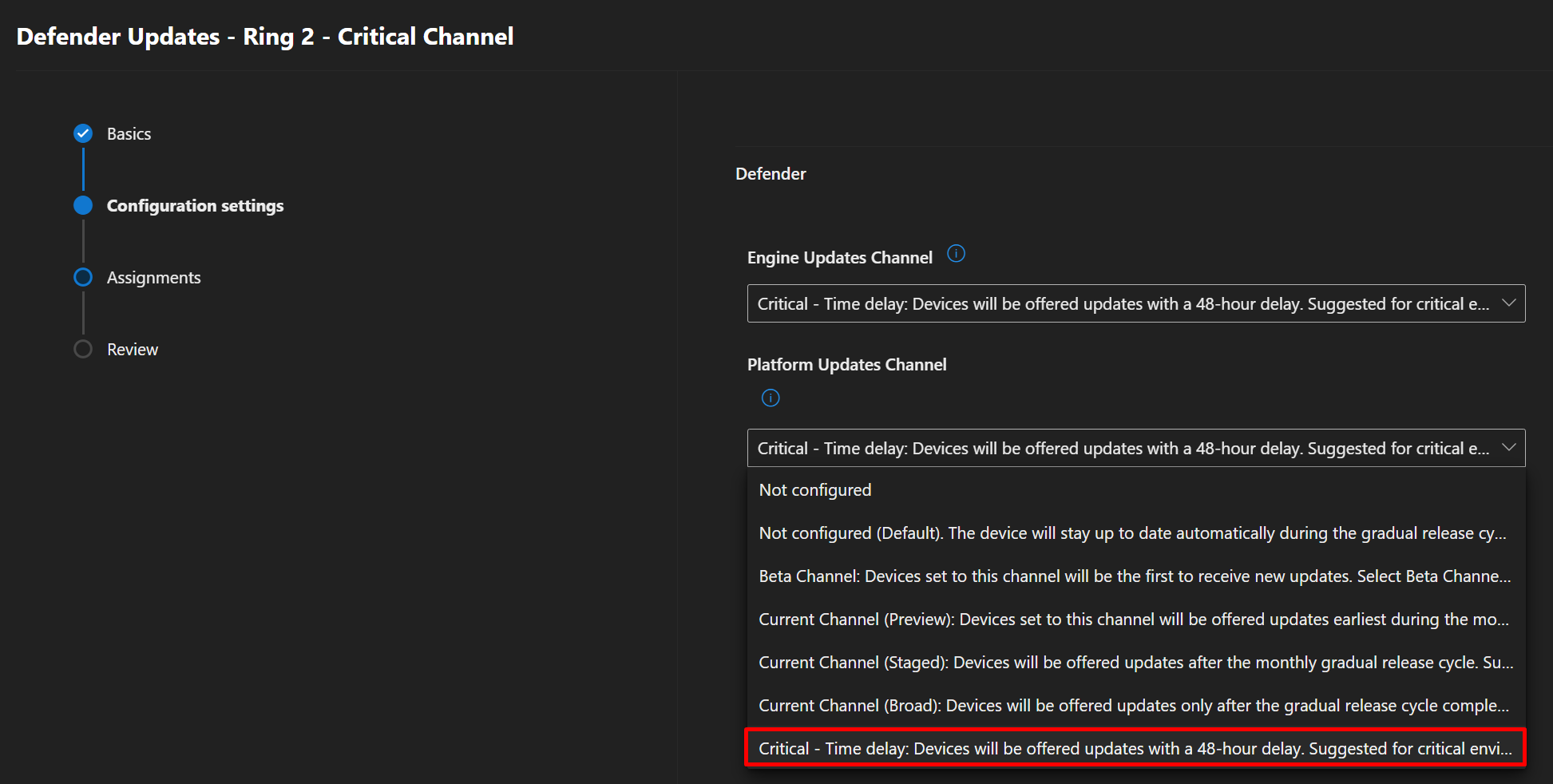
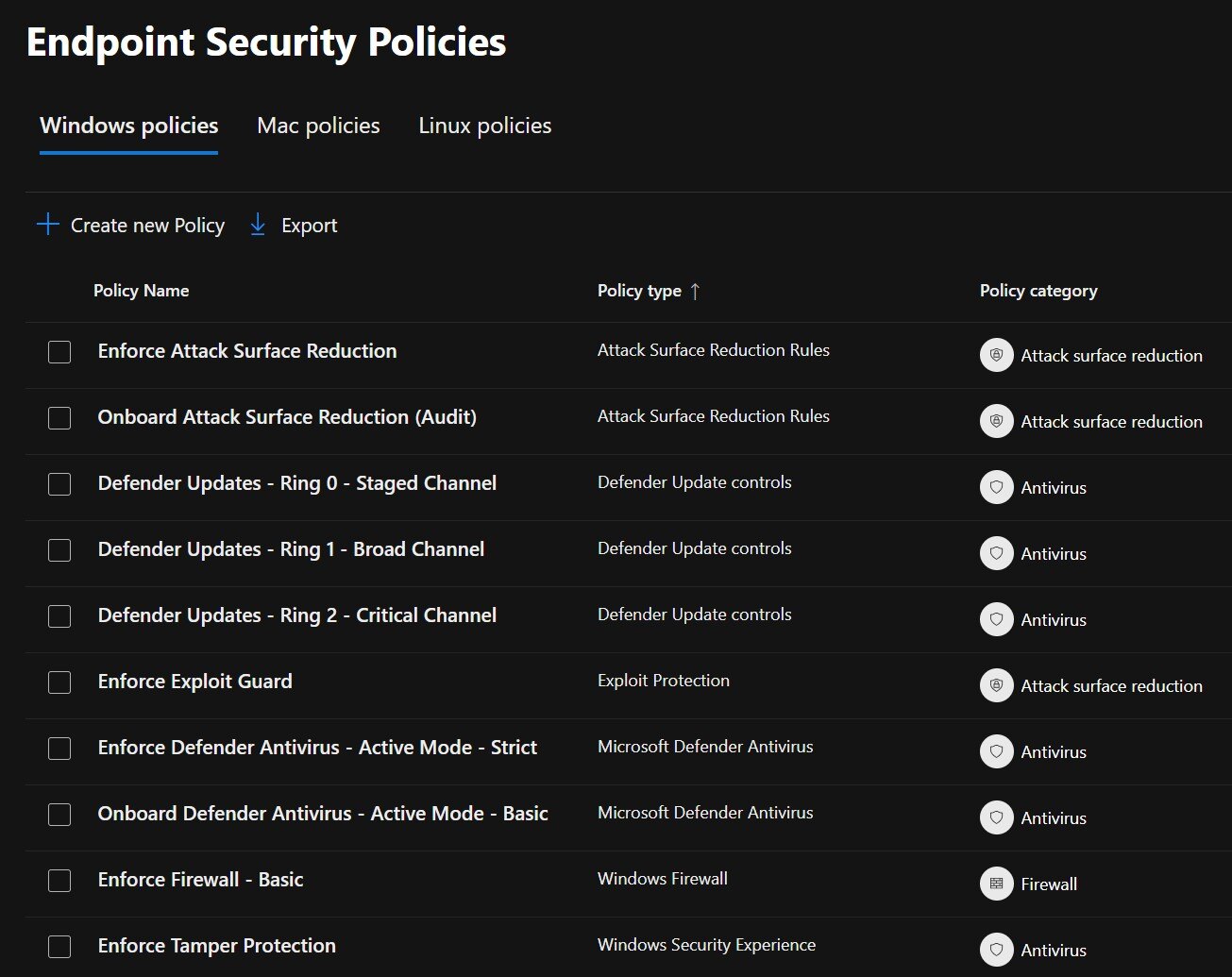
The purpose of the repository is to provide baseline settings for rapid deployment of Microsoft Defender for Endpoint using management policies. If your organization has Microsoft Defender for Endpoint P2 (which is part of the Microsoft 365 A5, E5, and F5 bundles, as well as in uplift SKUs like Microsoft 365 Security A5, E5, and F5, as well as the standalone Microsoft Defender for Endpoint P2 SKU -- see our licensing matrix for more information), using this repo provides files to populate configuration areas in Intune such as Endpoint Security, Antivirus Configurations, Intelligence Update Rings, Tamper Protection, Basic Firewall enablement, and Attack Surface Reduction Rules.
Conclusion
The recent incident involving CrowdStrike highlights the potential risks associated with relying on a single cybersecurity provider and underscores the importance of having a robust mechanism for managing updates. Microsoft Defender for Endpoint offers a reliable alternative with its update rings feature, providing businesses with better control over their cybersecurity deployments. Additionally, the availability of a dedicated GitHub repository for rapid onboarding makes it easier for businesses to make the switch, ensuring they can protect their endpoints without facing significant disruptions. For businesses looking to enhance their cybersecurity posture, Microsoft Defender for Endpoint represents a sound investment in stability, security, and scalability.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Microsoft Defender For Endpoint Standalone is Now Available! (Formerly MD ATP)
Microsoft Defender for Mobile Endpoints
No Comments Yet
Let us know what you think