Top 3 Anti-Ransomware Guards for Windows 10 in 2020
Ransomware attacks are increasing exponentially. Infused Innovations sees this trend continuing into 2020 and we want to share a few ways that we protect our clients. The three anti-ransomware guards for Windows 10 that we'll look at today are:
- Windows Defender Credential Guard
- Windows Defender System Guard
- Controlled Folder Access
I've selected these three tools because they cause the most problems with the Microsoft Security Compliance Toolkit (MSCT) and Security Baselines in Microsoft Intune. However, they provide some of the greatest protections against ransomware in Windows 10. Aside from the customizations that we'll discuss in this article, we typically suggest most of the remaining Microsoft recommended baselines.
These three Windows security tools should be used as part of your organization's defense-in-depth cybersecurity strategy. I highly recommend starting with our suggestions listed in our guide for ransomware protection before implementing the tools in this post.
Microsoft Security Compliance Toolkit
The security baseline recommendations in the MSCT are a great time-saving resource for cybersecurity professionals. Microsoft's baselines for anti-ransomware configurations are great for IT pros that are unfamiliar with Windows 10 Credential Guard, System Guard, Exploit Guard, and Device Guard. The only problem is that the out-of-the-box settings require testing and customization for most organizations.
The default MSCT and Intune Security Baselines are very similar to Windows S mode, in that all Microsoft apps work great, but any other vendors will need to be whitelisted to use the full feature set. (Also, VBS / BitLocker is broken in the out-of-box configuration on some newer hardware.) But the virtualization-based security (VBS) tools in Windows 10 are absolutely worth implementing to protect against ransomware.
Note: this guide uses the Intune Security Baselines as a reference and not the MSCT baselines. While they should be the same, there is some drift in the policies.
Requirements for Virtualization Based Security
You'll need to be on Windows 10 Enterprise or Windows 10 Education. This requires a Windows 10 E3/A3 or greater subscription. Head over to our Microsoft 365 licensing comparison to see which bundles include the licensing you need.
I also suggest using Windows 10 build 1903 or newer. Build 1809 has an issue with running Windows Defender Application Guard in audit mode where it basically causes Edge to crash every 10 seconds.
Build 1809 added a ton of great security features like Windows Defender Exploit Guard. This is the updated version of the Enhanced Mitigation Experience Toolkit (EMET) that was popular for making sure Windows 7 met compliance requirements. I've met folks needing to adhere to PCI-DSS, HIPAA, FEDRAMP, or NIST frameworks that were holding off on upgrading to Windows 10 until the new version of EMET was released. As a result, I don't recommend using any builds of Windows 10 prior to the 1809 Fall Creators Update.
1. Windows Defender Credential Guard
<
Mimikatz is a hack tool that can steal your credentials in under a second if you're not using Credential Guard by exploiting Pass-the-Hash or Pass-The-Ticket attacks. Credential Guard virtualizes the Windows credential vault to block the theft of NTLM password hashes, Kerberos Ticket Granting Tickets, and credentials stored domain credentials. Watch the entire video above to see a side-by-side comparison of two machines with/without Credential Guard enabled.
Unfortunately, the Microsoft Security Baselines enable Credential Guard in a way that will cause your TPM chip to fail and prevent you from enabling BitLocker on certain hardware. I've only seen this happen on the Surface Pro 7, Surface 3 laptop, and a few Dell & HP boxes. The exact TPM error message in the Event Viewer will be similar to: The device cannot start. (Code 10)
If you look in System Information, you will see the following message if you try to use the Security Baselines to enable Credential Guard:
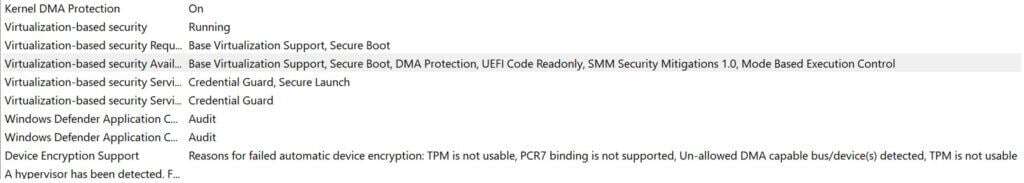
Reasons for failed automatic device encryption: TPM is not usable, PCR7 binding is not supported, Un-allowed DMA capable bus/device(s) detected, TPM is not usable.
To deploy credential guard on newer machines, you must disable VBS policies in the security baseline and use the credential guard PowerShell tool to enable them instead.
Once you've disabled Credential Guard and all VBS related guards in your policy, you have to download the Windows Defender Device Guard and Windows Defender Credential Guard hardware readiness tool. Then use the following PowerShell to enable VBS instead.
# Download this script https://www.microsoft.com/download/details.aspx?id=53337 # and extract/rename the PowerShell file to match the below if the version has changed: c:\temp\DG\DG_Readiness_Tool_v3.6.ps1 # If you've already tried deploying the Microsoft security baselines, you must disable VBS by running: c:\temp\DG\DG_Readiness_Tool_v3.6.ps1 -Disable -AutoReboot # The machine will reboot. Press F3 four times to disable credential guard and VBS pre-boot. # Once back in the OS or if you're enabling VBS for the first time, run: c:\temp\DG\DG_Readiness_Tool_v3.6.ps1 -Enable -AutoReboot #The line above is how you should implement Credential Guard for all new deployments until the baselines are fixed. # Reboot two or three times to make sure BitLocker and TPM stay activated.
Now when you look in System Information, you will see that Device Encryption meets the prerequisites and all the VBS Guards are enabled.
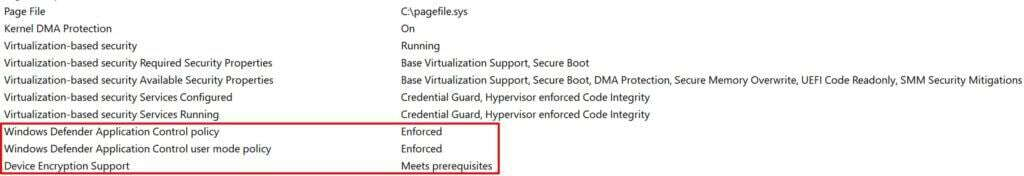
Why you have to enable Credential Guard this way is beyond me. I'm hoping the next baseline revisions will address this issue. Here is a good forum thread about other hardware devices having similar issues: https://borncity.com/win/2019/08/17/windows-10-v1903-bitlocker-issue-tpm-2-0-drops-error-10
Credential Guard Warning
WARNING: enabling Credential Guard will break the following environments:
- MSCHAPv2 pass-through authentication for 802.11 or Always-on VPN connections
- Username/password will still work but the user must manually enter it instead of it being read automatically from the credential vault.
- The fix is to use certificate authentication instead. Yes, you'll have to deploy PKI if you don't have it already.
- Some third-party tools that try to pass-through Windows Authentication to their application for seamless sign-on.
2. Windows Defender System Guard
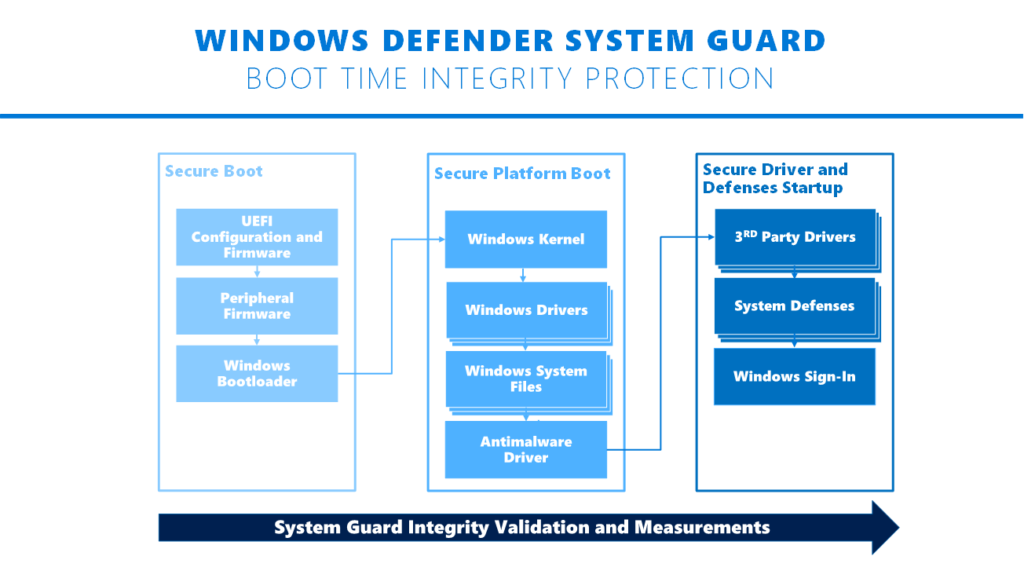
You need to enable System Guard to prevent pre-boot attacks that can bypass Credential Guard. There's little to no risk enabling System Guard. The PowerShell script in section 1 will enable System Guard too. All you need to do is make sure your PC is using UEFI to boot before enabling System Guard.
If you're interested in the nitty-gritty details, check out the Microsoft documentation.
3. Controlled Folder Access
The last area we'll cover is Controlled Folder Access. This powerful tool is only available in Windows 10 Enterprise and Education editions and is a great way to prevent ransomware attacks. It works by only allowing whitelisted applications to write directly to your Desktop and Documents folder. The problem with that is the OOB configuration will likely block every desktop application that you use outside of the Office 365 ecosystem.
Rather than learning how to properly whitelist applications, I've seen numerous forum discussions and software support engineers suggest that you should disable the feature. That's dumb. If you paid for monthly monitoring of your Ring/Nest home security system, but your maid/nanny/roommate/in-laws/children can't figure out how to disable the alarm whenever they show up, would you just leave the alarm always off? Don't be dumb. If you're paying for a security service, use it correctly.
One major culprit that routinely tells their users to disable Controlled Folder Access is Adobe for their Creative Cloud Suite. Running the following PowerShell script resolves most of Adobe's issues with Controlled Folder Access:
#Create an array to add all exe files in a path and whitelist them in controlled Folder Access
$programs=@()
#Modify the path to the folder directory that contains the executables of the applications that you want to whitelist, in this case we're targeting Adobe.
Get-ChildItem -path 'C:\Program Files\Adobe\*.exe' -Recurse|%{$programs+=$_.versioninfo.filename}
#Then add them as a whitelisted app in controlled folder access
$programs| % {Add-MpPreference -ControlledFolderAccessAllowedApplications $_}
One application that is still bricked after running the above script is Adobe After Effects. On my machine, I have to "run as" another 'dummy' account that has Controlled Folder Access disabled, then save to a shared directory on the workstation that the dummy account has access to. Needless to say, this is also dumb. But it works. Ideally, Adobe should just fix their shit to work securely. I don't have high expectations though. See Adobe Flash as a case-in-point.
Another method to whitelist apps is to scrape the Event Log for blocked applications. Then feed your hashtable into a foreach loop to whitelist them. WARNING: only run this script if you know the machine you're using is healthy. Otherwise, you may be whitelisting ransomware or other malware.
#Get all blocked applications in the recent event history
$appEvents = Get-WinEvent -FilterHashtable @{Path="$env:SystemRoot\System32\winevt\Logs\Microsoft-Windows-Windows Defender%4Operational.evtx";Id=1123}
$apps= $appEvents | % {$_.Properties[7]} | Sort-Object -Unique
#Whitelist all apps that were found in the recent event history
$apps| % {Add-MpPreference -ControlledFolderAccessAllowedApplications $_}
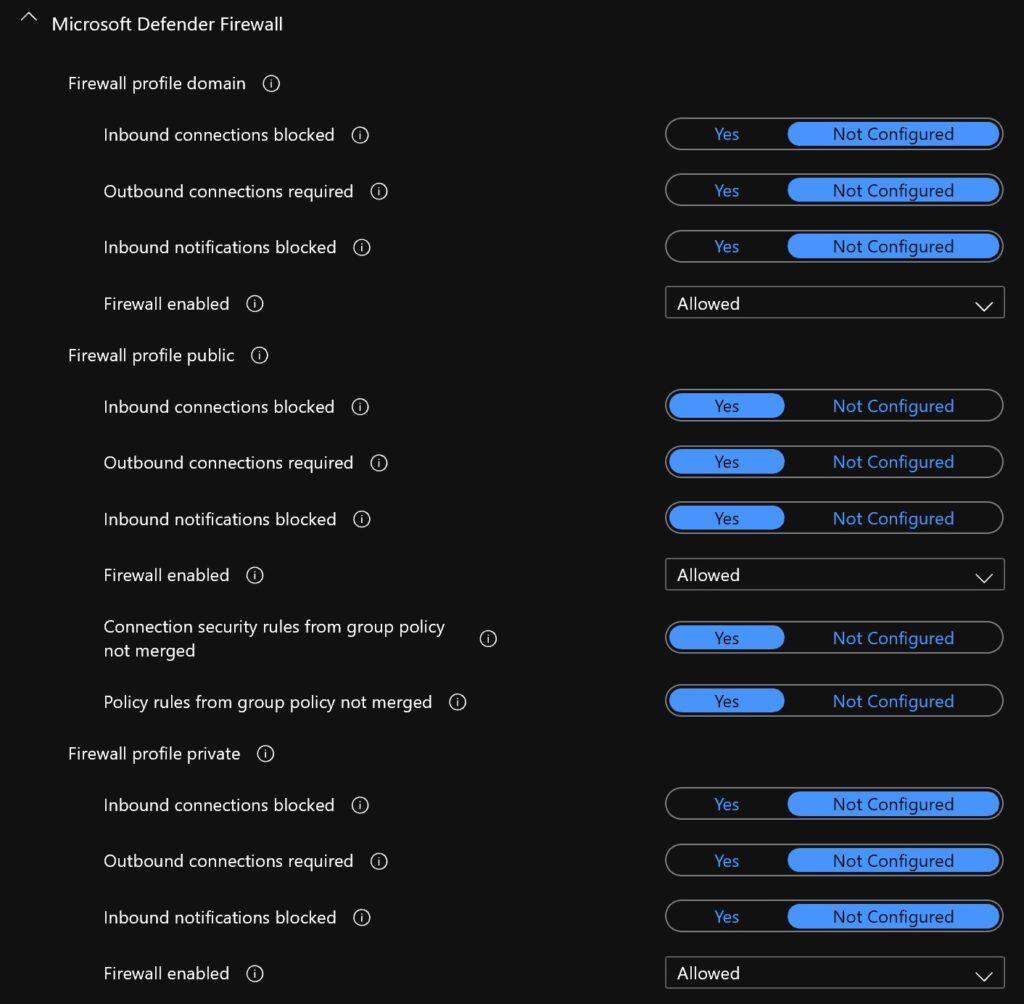
Bonus Configuration to Enable RDP for AADJ Machines
In the Intune Security Baselines, Remote Desktop is blocked by default for Azure AD Joined (AADJ) machines. However, if you're still running AD on-prem and your machine is hybrid AADJ, RDP will work for domain users. But for your cloud-only AADJ devices, there isn't a nice "Enable/Disable RDP" since AAD users are treated as local accounts. You basically need to disable all of the advanced security policies on private/domain networks in the Microsoft Defender Firewall to allow RDP to work on AADJ devices. (Again, this isn't an issue for domain users on domain-joined computers.)
Closing Thoughts on Anti-Ransomware Guards for Windows 10
You can protect your organization, your users, and your data from ransomware. I've heard too many people claim ignorance that there is nothing that can be done to protect yourself against modern cyber-attacks.
Yes, you will likely suffer some sort of security breach this year. If you have a defense-in-depth strategy built on top of a zero-trust framework, it will likely be insignificant though. For anyone else that's relying on positive thinking to protect their data, hit me up by signing up for a free Microsoft 365 cybersecurity review.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Guide to Deploy Gen2 VMs in Azure

Defender Announcements from Microsoft Ignite 2022
No Comments Yet
Let us know what you think