Step-by-Step Guide to Securing Windows Virtual Desktop in Azure with Conditional Access and MFA
One of my biggest complaints about using Azure AD P1 to issue Azure MFA challenges on a traditional RDS deployment via RADIUS authentication is that it issues an MFA challenge on every login. That’s almost as frustrating as trying to understand Microsoft Licensing.
Fortunately, securing Windows Virtual Desktop in Azure with Conditional Access and MFA is a breeze and dramatically improves the user experience!
Requirements for Securing Windows Virtual Desktop in Azure with Conditional Access and MFA
Here are a few prerequisites that you’ll need already configured in your lab:
- An Azure CSP Subscription from Infused Innovations (Or any Azure Subscription will work too)
- An existing deployment of Windows Virtual Desktop in Azure
- In addition to the Windows Virtual Desktop licensing requirements, you’ll need one of the following SKUs for conditional access and Azure MFA:
- Azure AD P1 / P2
- Azure AD P2 includes risk-based conditional access
- Enterprise Mobility + Security (EM+S) E3 / E5
- EM+S E5 includes risk-based conditional access
- Microsoft 365 E3 / E5
- The Identity Threat Protection add-on SKU adds risk-based conditional access to Microsoft 365 E3
- Microsoft 365 E5 includes risk-based conditional access
- If you don't own the proper licensing yet, you can compare all Microsoft 365 licensing options on our blog
- Azure AD P1 / P2
- Consider reviewing our Getting Started with Conditional Access and Azure MFA guide if you’re not familiar with conditional access
Configure Windows Virtual Desktop in Azure with Conditional Access and MFA
When you integrate any application with Azure SSO as either a SAML 2.0 endpoint or Enterprise Application, it’s simple to create a conditional access policy to enforce MFA challenges for that application.
Create a new Conditional Access Policy
- Navigate to the Conditional Access blade in the Azure management portal: https://portal.azure.com/#blade/Microsoft_AAD_IAM/ConditionalAccessBlade/Policies
- Click New Policy and name it: MFA for Windows Virtual Desktop
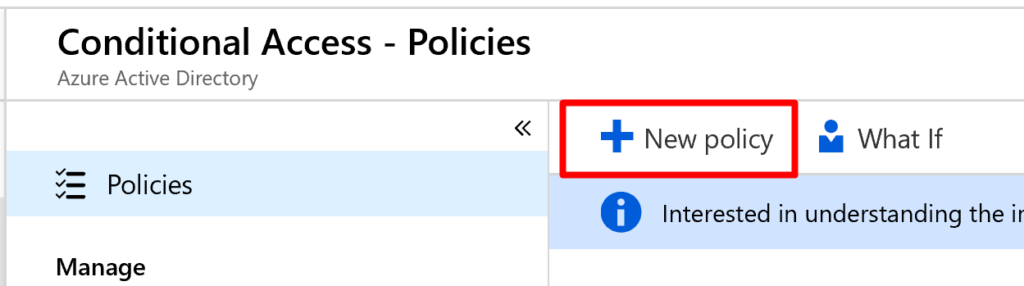
- Under Assignments, target All Users or choose a pilot group
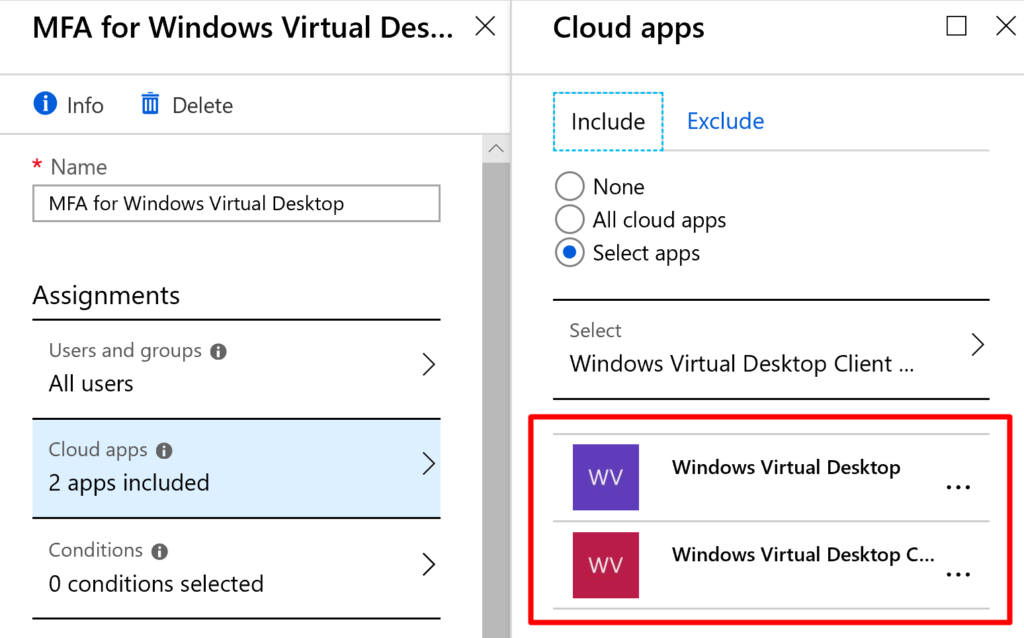
- SelectCloud Apps search for Windows Virtual Desktop and select the apps that are registered in your tenant:
- Under Conditions exclude Devices marked as compliant to allow your enrolled and healthy devices to bypass MFA challenges:
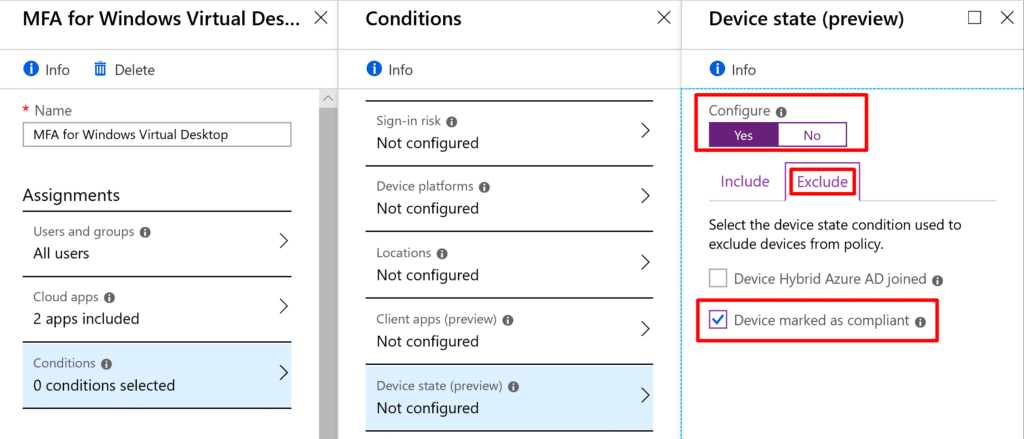
- Note: You can optionally target risky sign-ins only. Or if you’re using thin clients at an office, you might want to exempt a trusted location.
- Under Access Control select Require multi-factor authentication
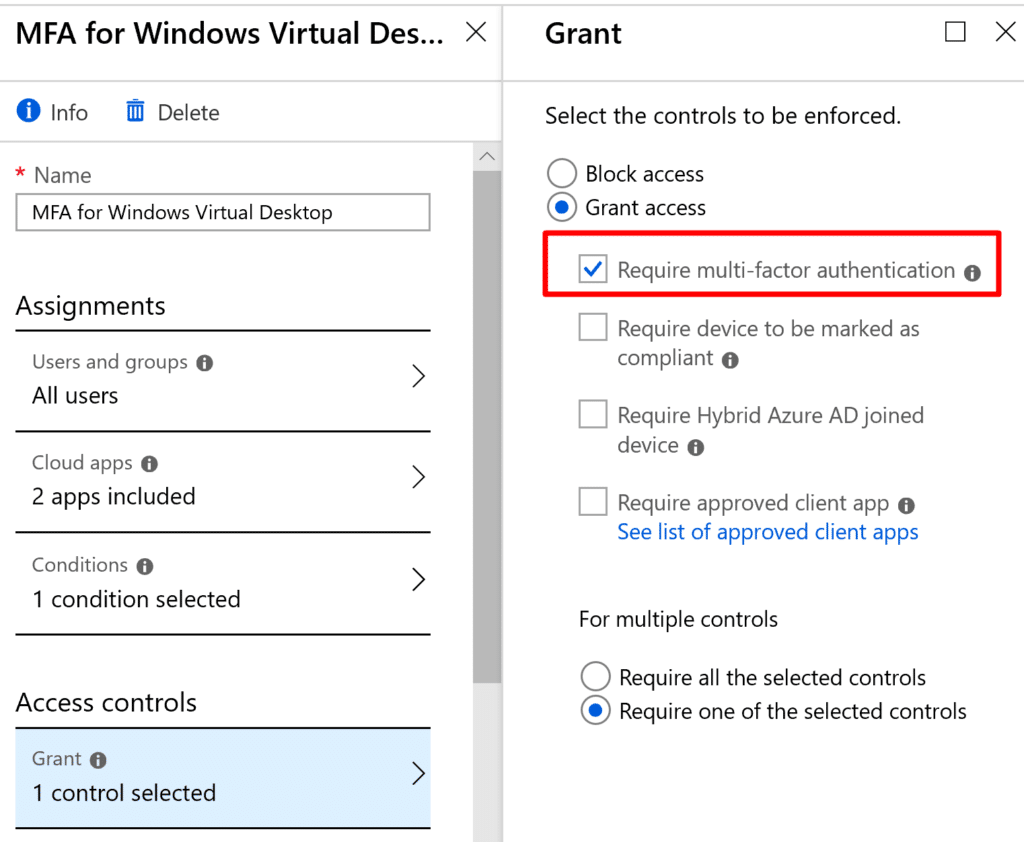
- Click Save and make sure you enable the policy
- Test your policy by logging into https://rdweb.wvd.microsoft.com/webclient/index.html from an unmanaged computer
Closing Thoughts on Securing Windows Virtual Desktop in Azure with Conditional Access and MFA
The new Windows Virtual Desktop service delivers exactly the multifactor authentication experience that I want to deliver to all our clients at Infused Innovations. I can allow users to bypass MFA when they’re accessing corporate resources in an approved environment; otherwise require an MFA challenge when they’re not.
It takes less than 15 minutes to secure Windows Virtual Desktop in Azure with Conditional Access compared to at least two hours to configure the Azure MFA extension with NPS to protect a traditional RDS deployment. (That time estimate is assuming you’ve deployed RDS with NPS before.) That is extraordinary value with minimal effort!
The improvements that Microsoft continues to build into their cloud offerings are delivering enterprise-class security and features at values that any SMB can afford. Checkout our WVD pricing guide for additional details on the hidden costs of Windows Virtual Desktop.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts

Palantir Technologies and Microsoft Partnership a Game-Changer for Government AI
Microsoft's Azure Arc
No Comments Yet
Let us know what you think